

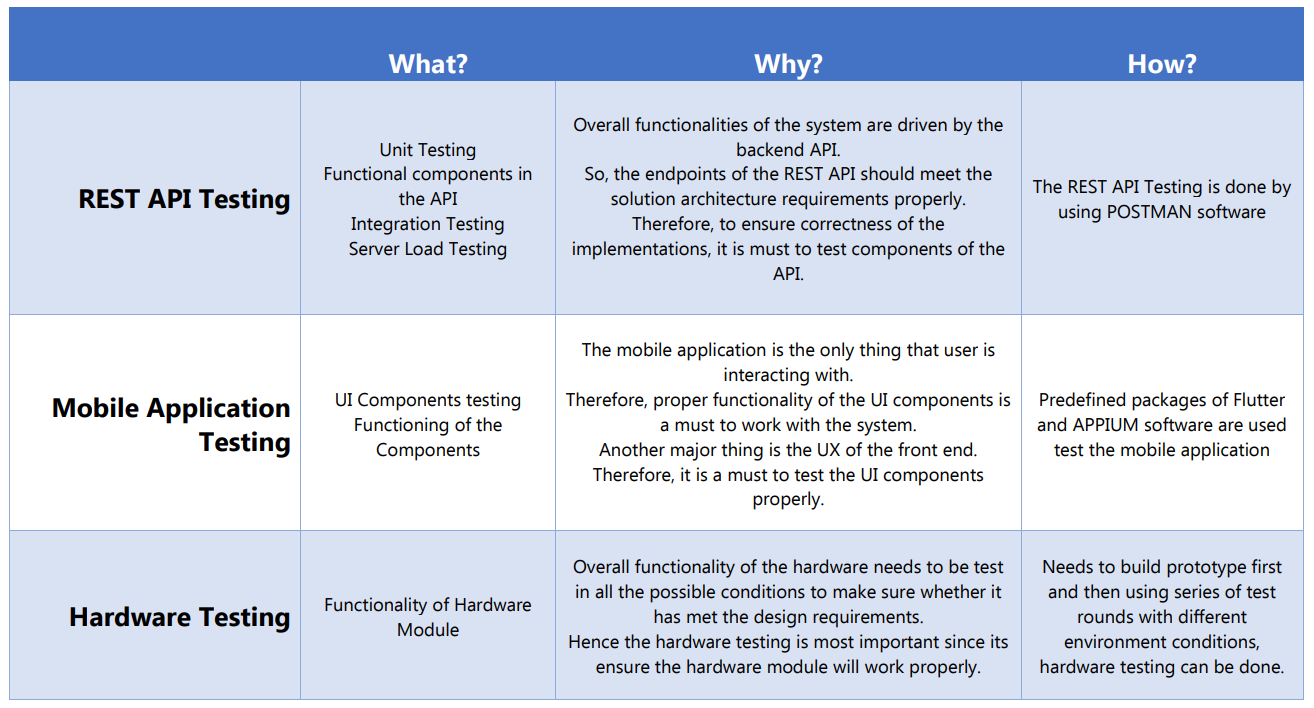
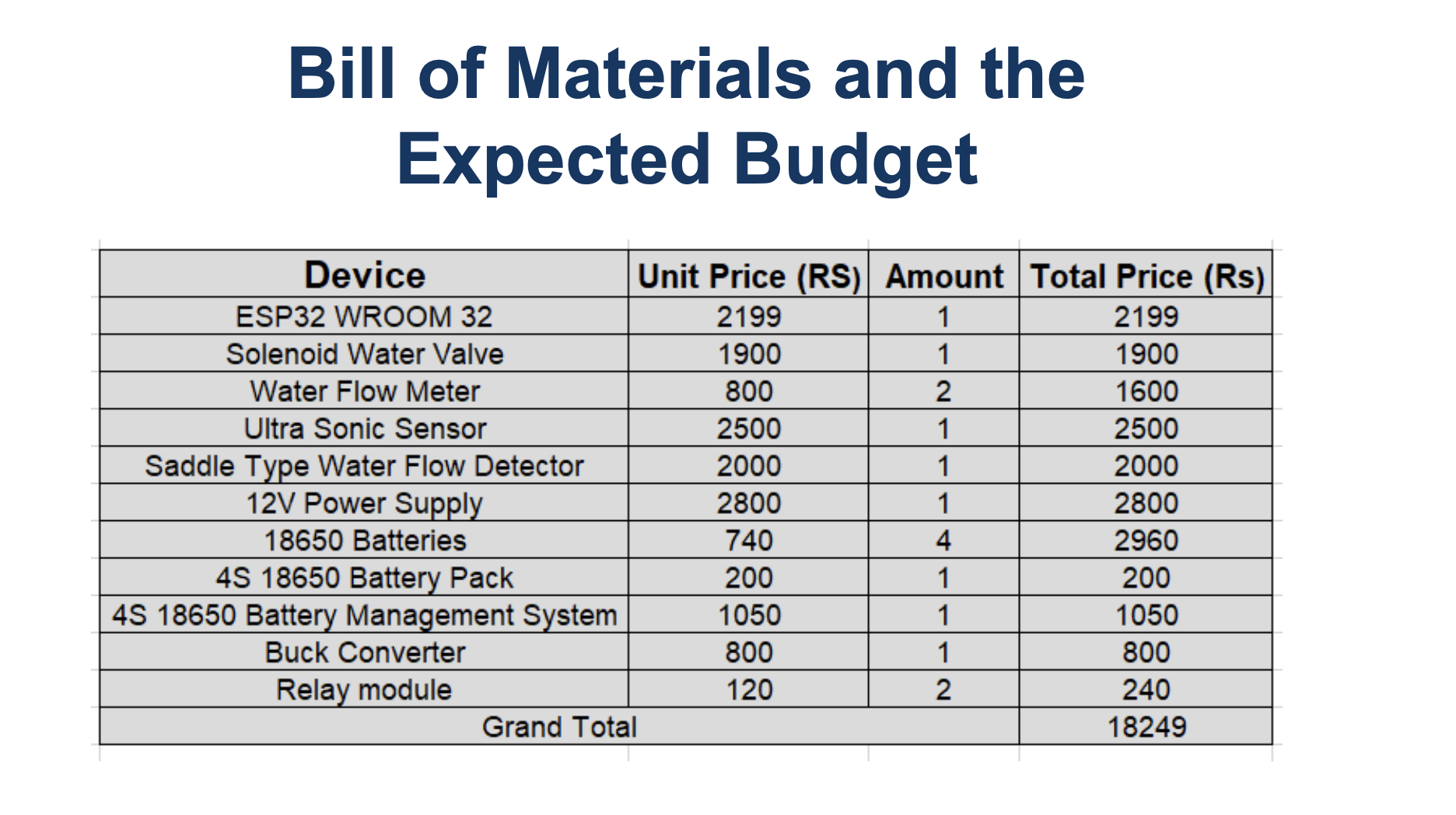
Solenoid Water Valve

Flow Rate Meter

Ultrasonic Sensor

Let's explore How this work
Project Repository
In the current scenario, water tanks lack intelligent monitoring and control systems,
leading to various issues and inefficiencies. The absence of smart technology results in
problems such as water wastage due to tank overflow, decreased water availability, and a
lack of user control and monitoring capabilities. Let's break down these issues:
Overflow Wastage:
Without proper monitoring, water tanks can easily overflow, leading to unnecessary
wastage of water. This not only contributes to resource depletion but also increases
water bills for users.
Reduced Water Availability:
Inefficient water usage and lack of real-time monitoring make it challenging for users
to optimize their water consumption. This can lead to situations where water
availability is compromised, especially during periods of high demand.
Limited User Control and Monitoring:
Users currently have limited control over their water tanks, relying on manual methods
to gauge water levels. This lack of control makes it difficult for them to manage water
usage effectively and respond promptly to changing needs.
Delayed Leak Detection:
Traditional water tanks lack the ability to detect leaks promptly. This can result in
water losses, structural damage, and increased repair costs. Timely detection of leaks
is crucial to preventing further damage and conserving water resources.
Inability to adapt to changing conditions:
Without real-time data and control capabilities, water tanks cannot adapt to changing environmental
conditions or unexpected events. Smart systems can respond dynamically to changes in water demand.



In the realm of traditional water management systems, users often grapple with issues of
reliability and trust.
Instances of overflowing tanks due to forgotten valve closures or delayed leak detection
not only result in property damage and increased utility bills but also erode the trust
users place in their water management systems.
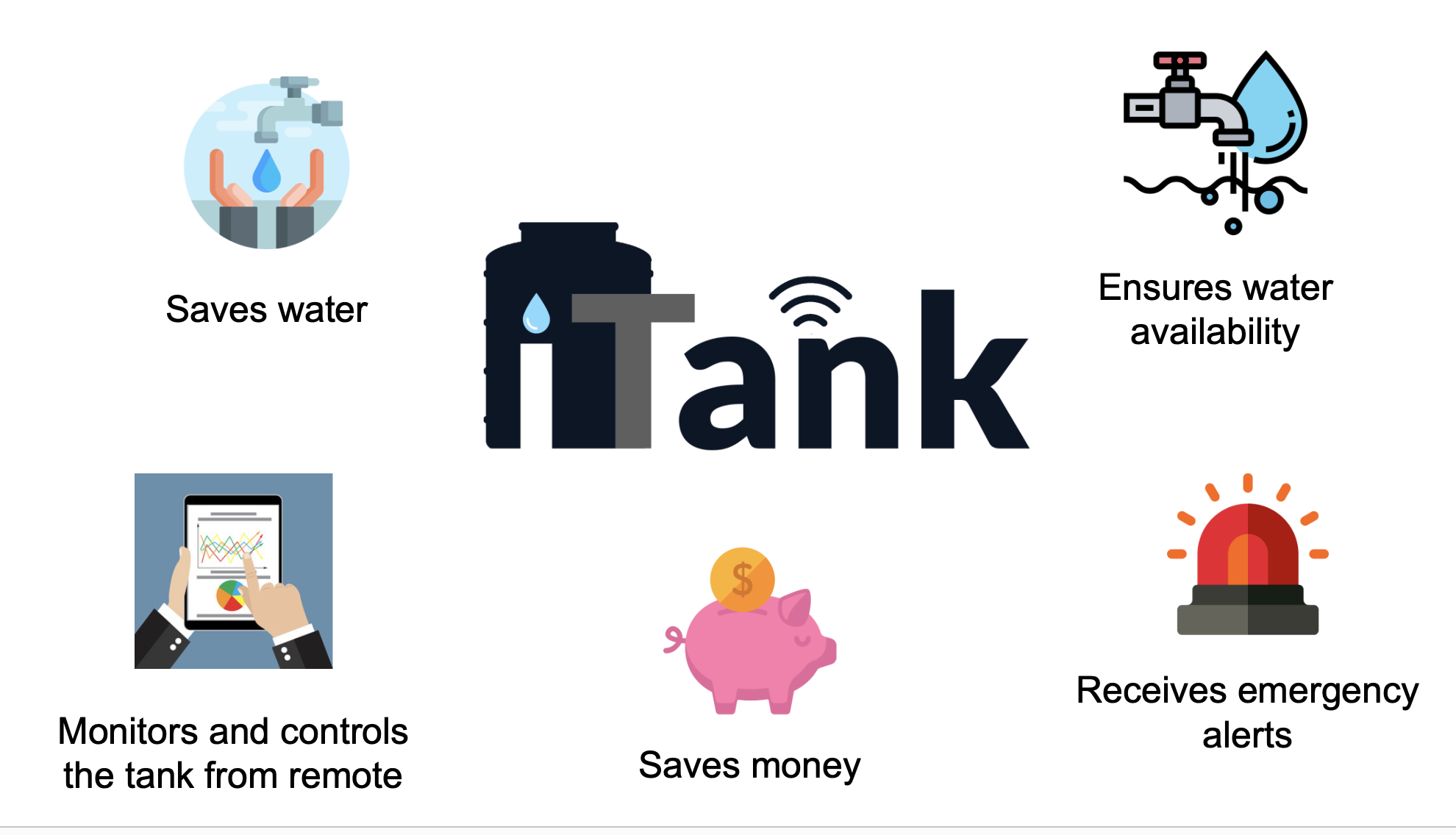
The introduction of a smart water tank revolutionizes this landscape, offering a
solution that goes beyond conventional methods. By providing real-time monitoring,
automated alerts ans notifications, and remote control features,
our smart water tank system ensures that users have complete confidence in the security
of their water resources.Our water tank system ensures the avaliability in the water tank. Just as customers and restaurant owners seek trustworthy
solutions in the realm of online food delivery services, our smart water tank aims to
instill the same level of confidence in users and empower them with a reliable, secure,
and efficient water management experience
Smart Water Tank:
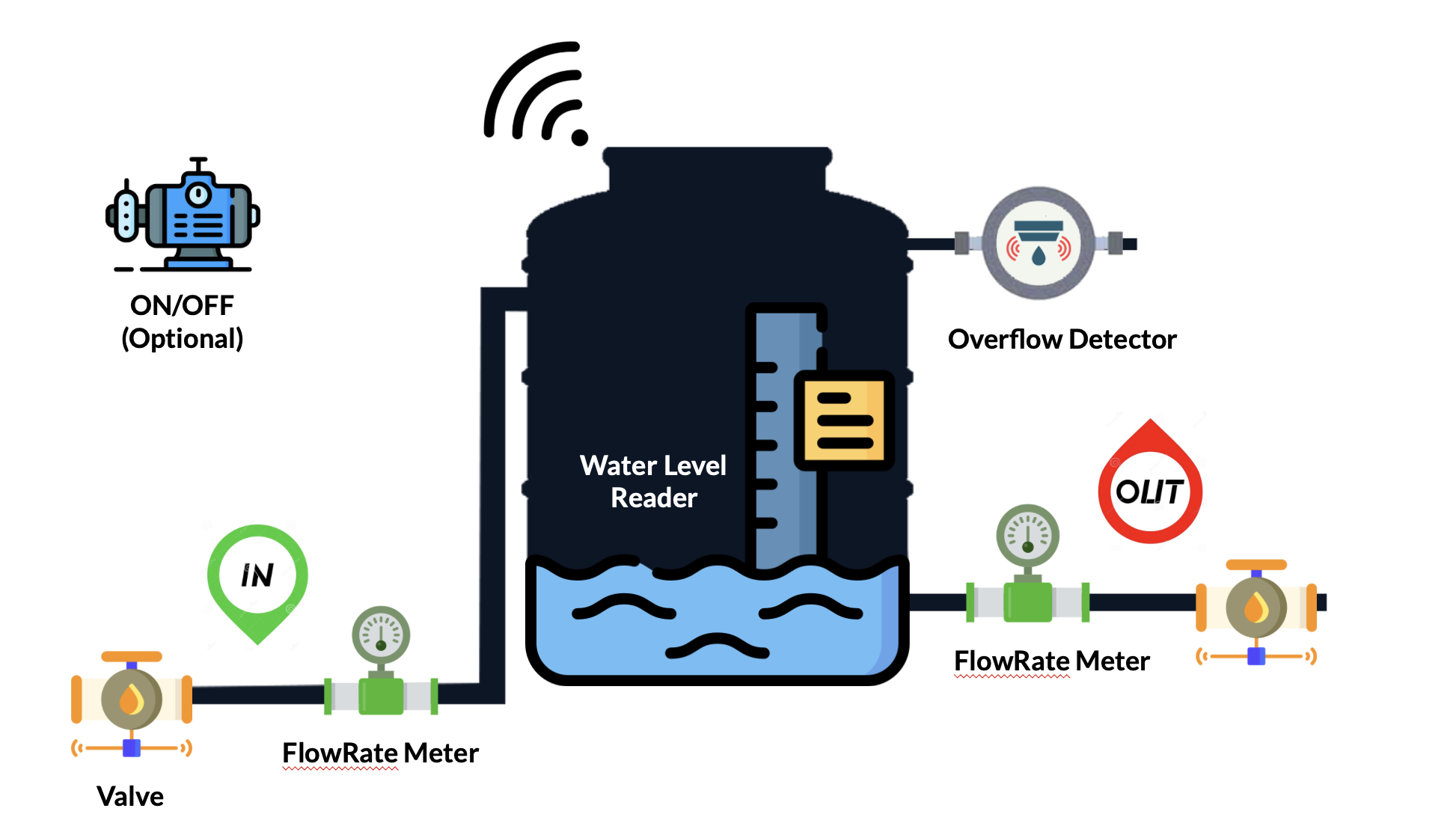
The implementation of a smart water tank involves integrating sensors and communication
devices to monitor and transmit real-time data on water levels and conditions within the
tank. This enables users to have accurate and up-to-date information about the status of
their water storage.
The use of cyber-driven valves allows for automated control of the water flow in and out
of the tank. These valves can be remotely operated based on the information gathered
from the sensors, preventing overflow and optimizing water usage.
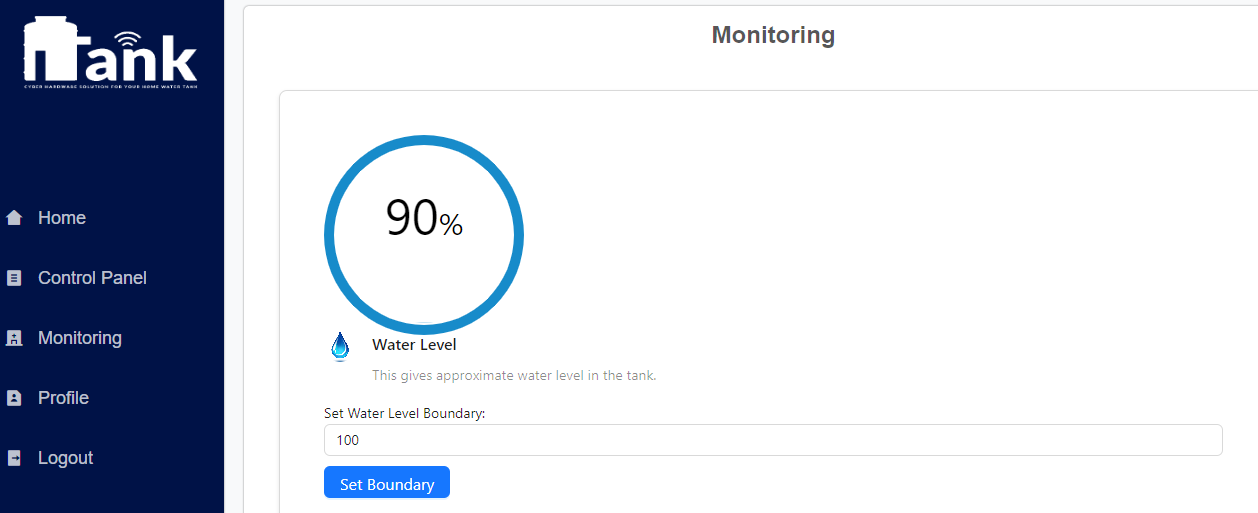
Water Level Sensors:
Water level sensors play a crucial role in providing accurate data on the current water
level in the tank. This information is essential for decision-making and ensuring that
the tank does not reach capacity, thus preventing overflow.
Water Flow Rate Monitoring:
Monitoring the water flow rate provides insights into the rate of water consumption or
distribution. This data is valuable for users to understand their water usage patterns
and for the system to optimize the operation of the cyber-driven valves.
Automated Control of Water Pump:
Implementing automation in the control of the water pump ensures that it operates
efficiently based on demand. The system can turn the pump on or off as needed, reducing
energy consumption and preventing unnecessary water pumping.

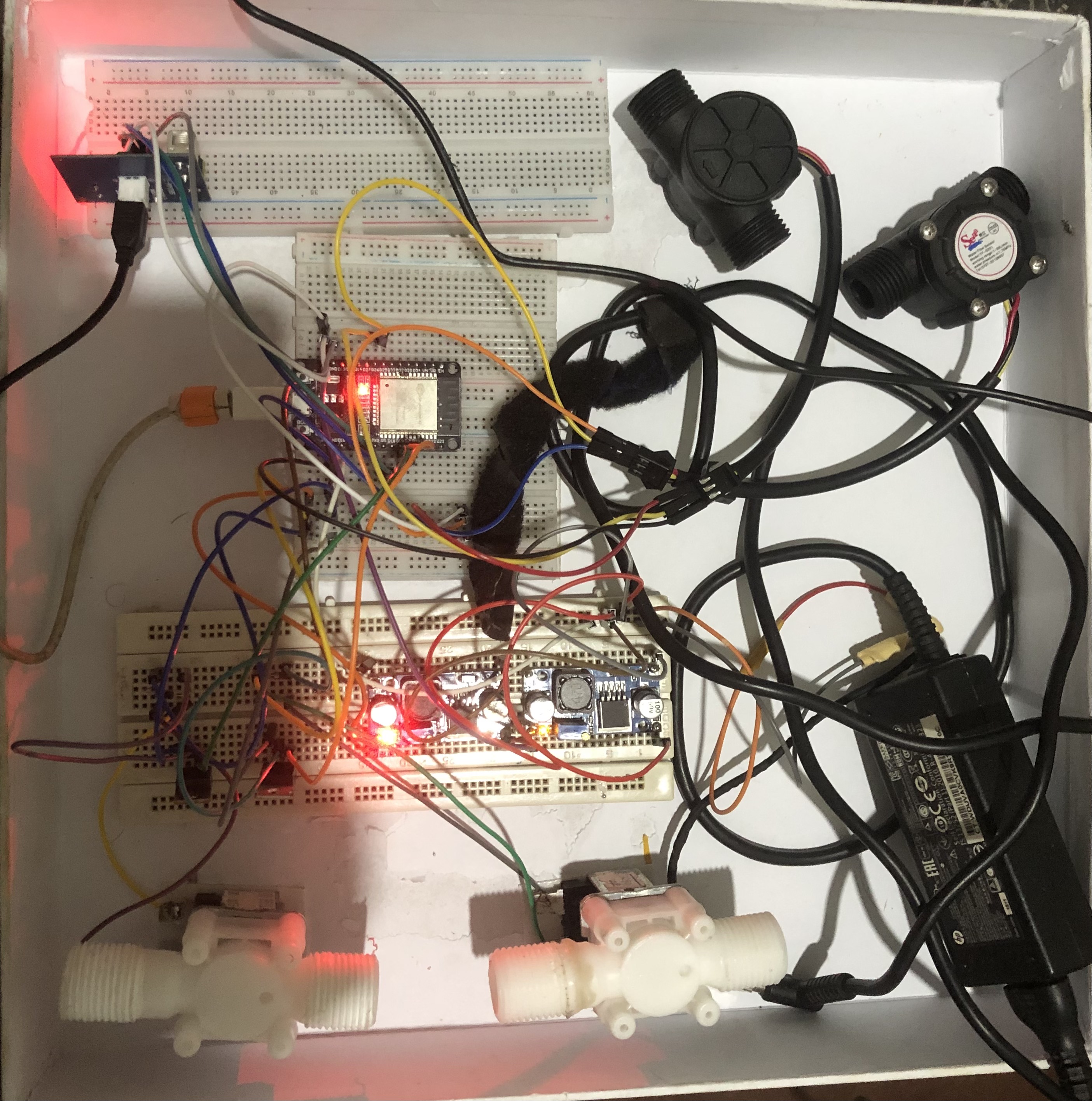
Components:
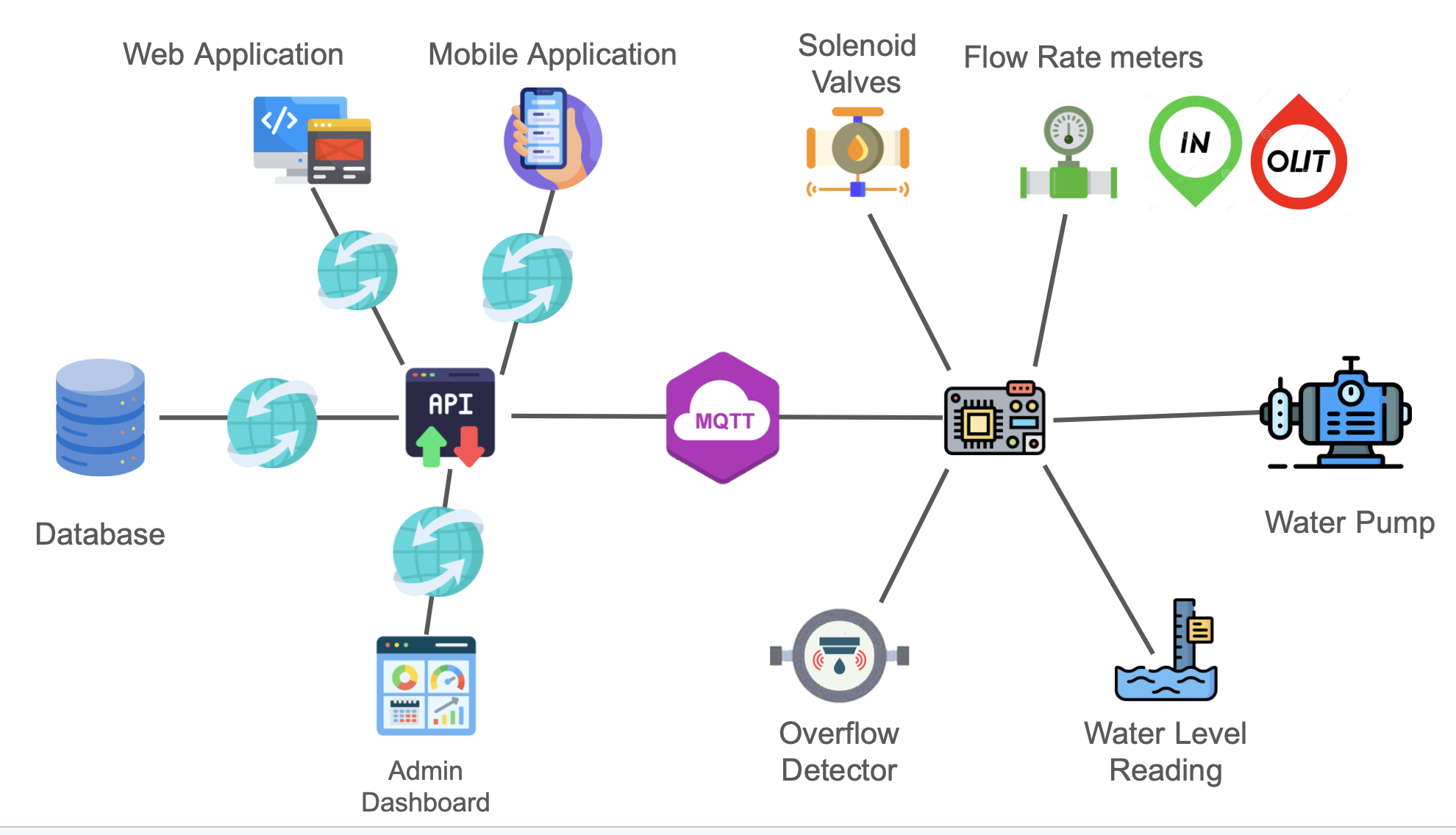
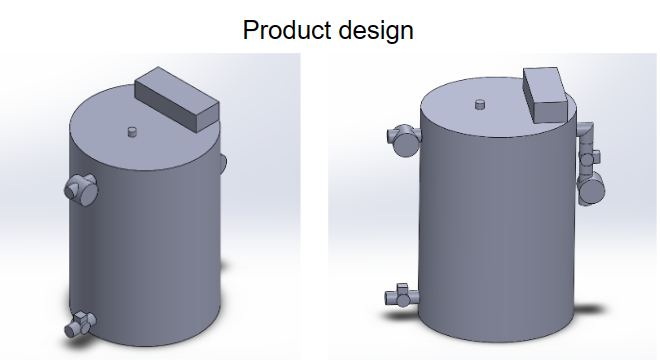
Water Tank:
Physical water storage unit equipped with sensors and communication devices.
Water Level Sensors:
Sensors placed at strategic points in the water tank to measure and transmit
real-time water level data.
Water Flow Rate Sensors:
Sensors installed in the water pipes to measure the flow rate and provide data
on water consumption or distribution.
Cyber-Driven Valves:
Valves controlled through a cyber-driven system that can be remotely operated
based on data from water level sensors and user input.
Automated Water Pump:
Water pump with automated controls that can be managed based on the water level
and demand.
Communication Infrastructure:
Network connectivity for data transmission between sensors, valves, water pump,
and the central control system.
Central Control System:
Cloud-based or on-premise system responsible for processing data, making
decisions, and managing the overall operation of the smart water tank.
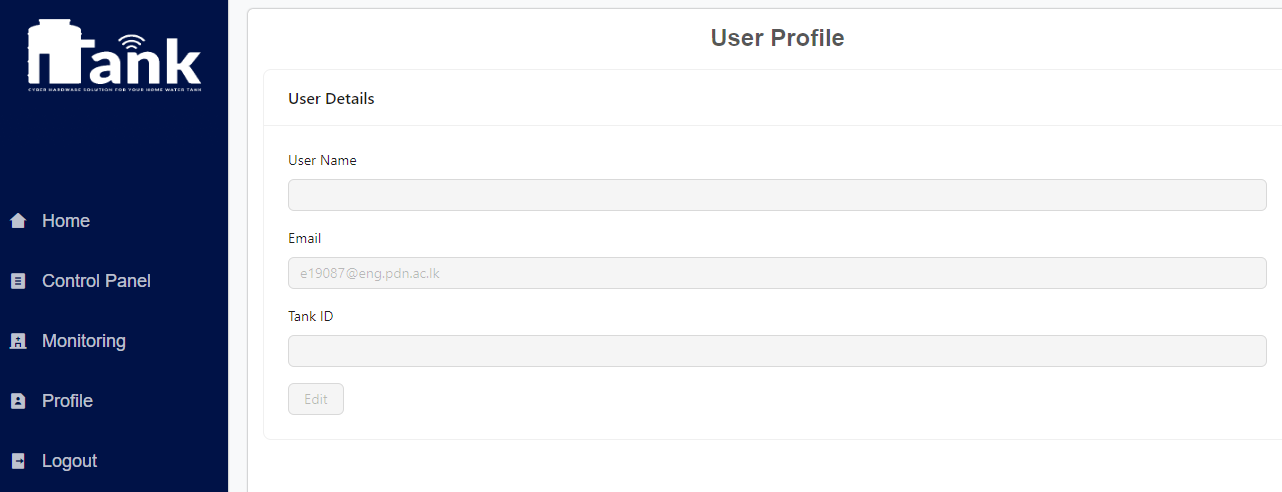
User Interface:
Web or mobile application providing users with real-time information, control
options, and alerts related to their water tank.

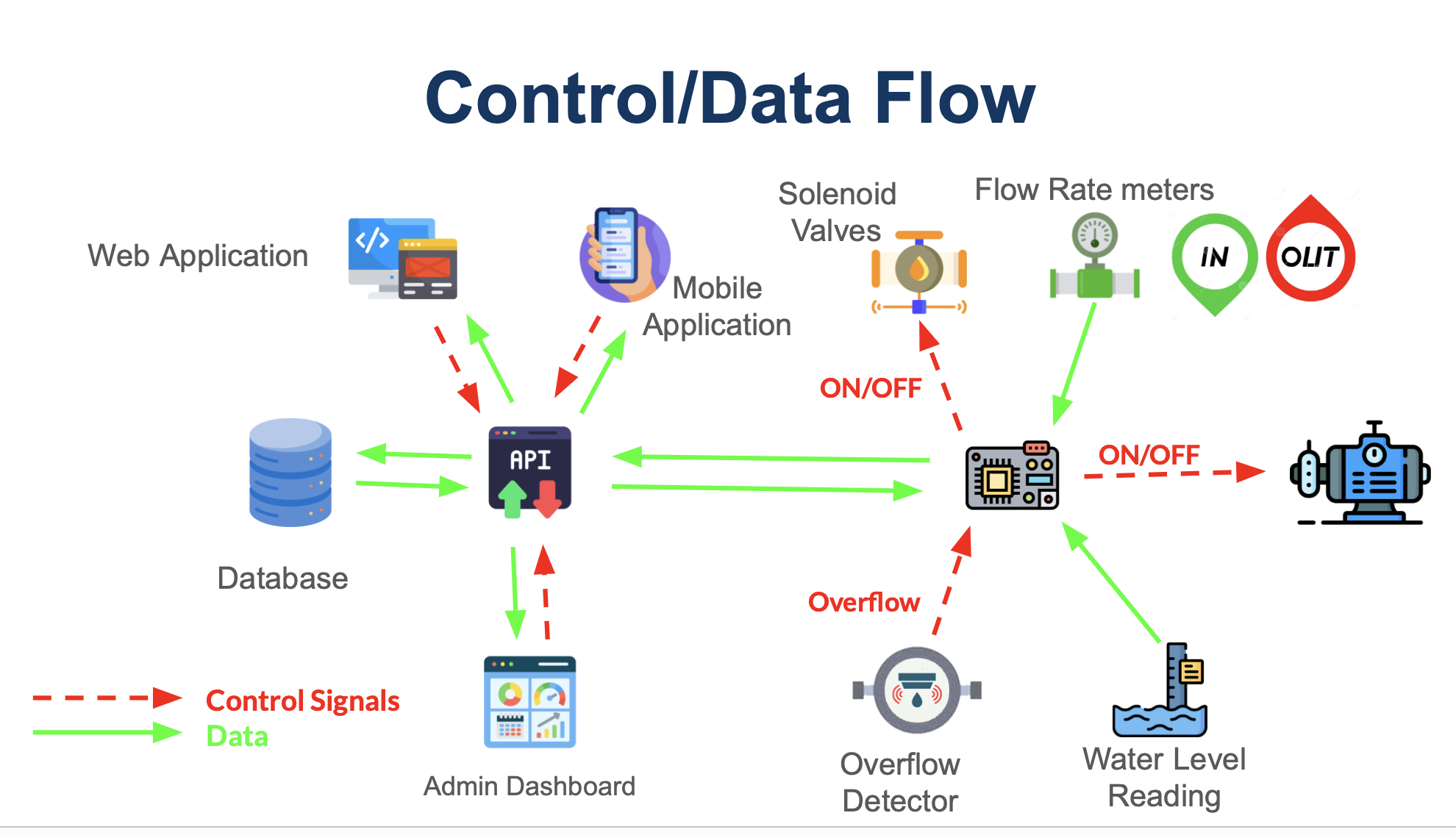
Data Collection:
Water level sensors and flow rate sensors collect real-time data on the water
level and consumption.
Data Transmission:
Collected data is transmitted to the central control system through the
communication infrastructure.
Decision Making:
The central control system analyzes the data to make decisions regarding valve
control, pump operation, and leak detection.
Valve Control:
Based on the water level data, the cyber-driven valves are controlled to
regulate the inflow and outflow of water, preventing overflow and optimizing
water usage.
Pump Control:
The automated water pump is controlled based on demand, ensuring efficient water
distribution and energy conservation.
Alerts and Notifications:
Users receive alerts and notifications through the user interface in case of
issues such as leaks, low water levels, or system malfunctions.
User Interaction:
Users can interact with the system through the user interface to monitor water
levels, control valves manually if needed, and access historical data.







React is a JavaScript library for building user interfaces, emphasizing the creation of reusable UI components for efficient development of web and mobile applications.

For the implementation of the mobile aplication, Flutter has chosen as it supports both android and IOS applications with single code base.

To built the API, Node.js javascript runtime enviroment is
used.
Single treaded non-blocking operations, make the speed of the
application much higher.and this sutable for real time processing

Mongodb: Non-Relational database Open Source Community Support Scalability Performance Optimization Data Security

AWS EC2 Service is used to host the API.
For the MQTT
connections, the AWS IoT Core is being plan to use.
Security is the most important thing in the IT world right now.
In our solution, we have deeply considered the security point of view of our system.
We have developed our system with the help of the following techniques to enhance the
application security in our solution.
For authentication purposes, our API uses the JSON Web Token to ensure integrity.
In the successful event of login, the user must receive a JWT, which is signed by the
server.
Whenever the client wants to communicate with API (after the login stage), it has to
pass that returned token with the
request.
If somehow the token is modified, API would deny access to the data.
User Inputs are the most common way to commit a malicious attack.
To prevent such scenarios, we validate the user input from both the front-end
application and the back-end API.
If inputs are not in the correct order, in the front-end, it denies the inputs. And from
the back-end, it denies the request.
Although we are using a relational database to work with data, we do not directly store
sensitive data on the database.
For that, we encrypt the sensitive data on the API with the help of well-known powerful
libraries and then store those in the database.
To ensure secure communication between the mobile application, and the API, we used the
HTTPS protocol to securely transmit the data.
With that, we can guarantee the message's integrity as well as the confidentiality of
the data.
In our API itself is secured with AWS EC2 security features. Hence the security of the
system is more in an advanced manner.
Hardware to hardware communication (API and the Microcontroller), we have used the MQTT
as the messaging protocol.
For that, we have currently used AWS IoT Core as an MQTT message broker, which is a
secured private message broker that requires certificate-based authentication for the
MQTT clients.

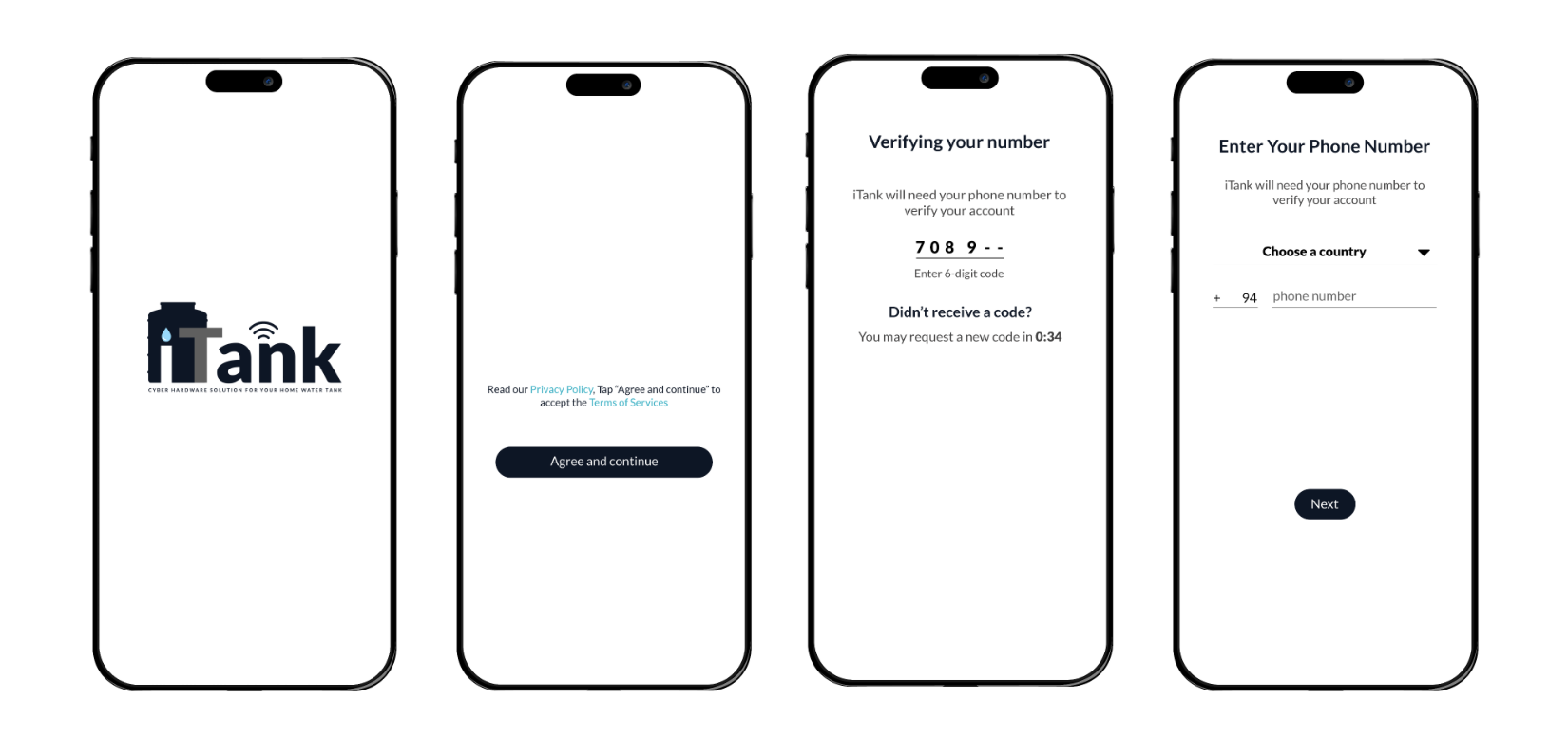
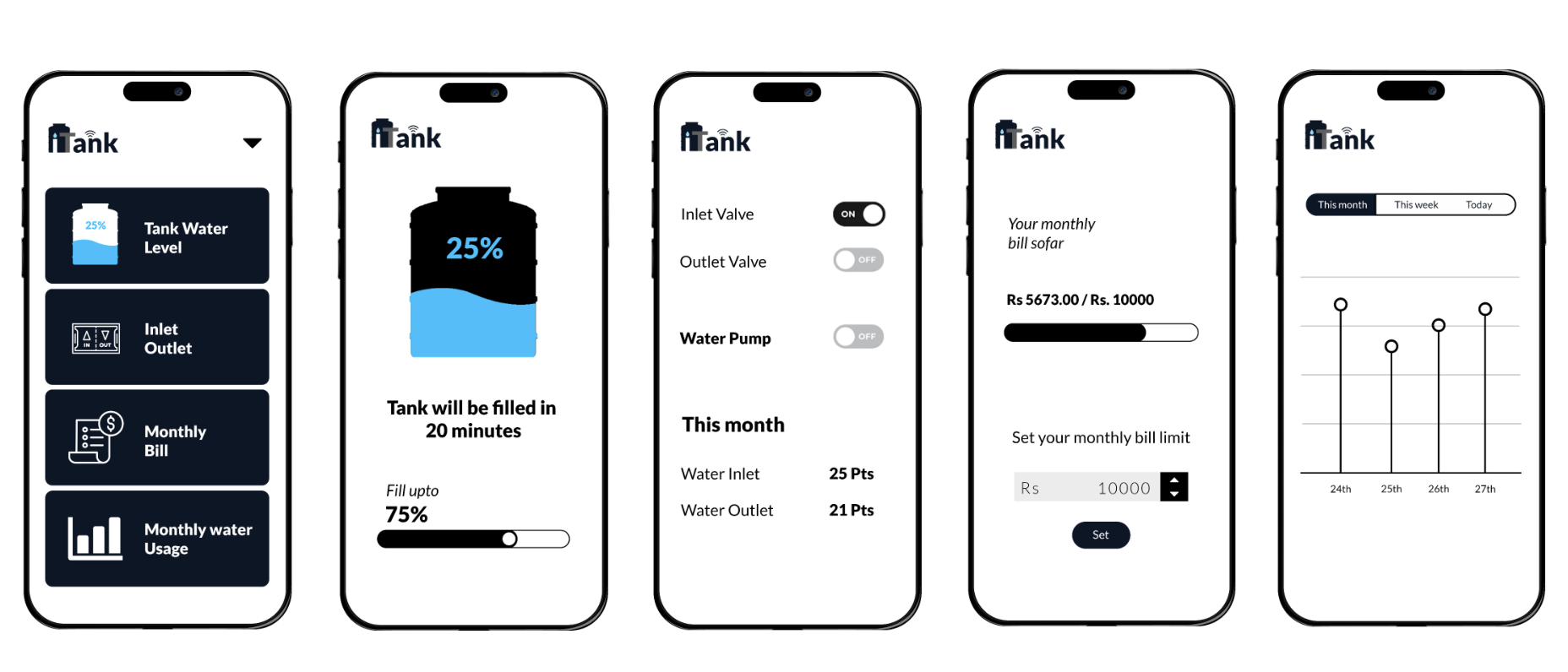
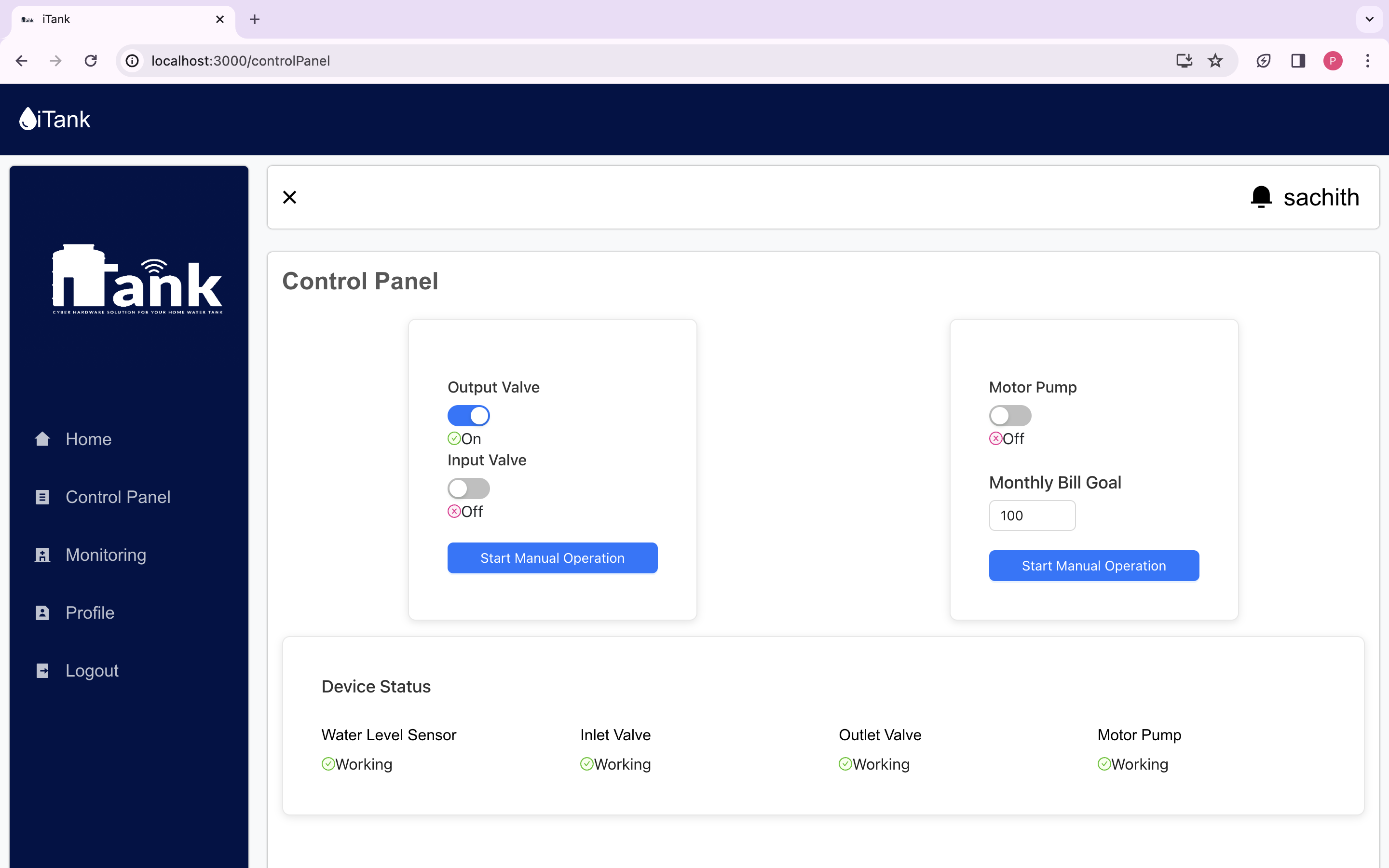
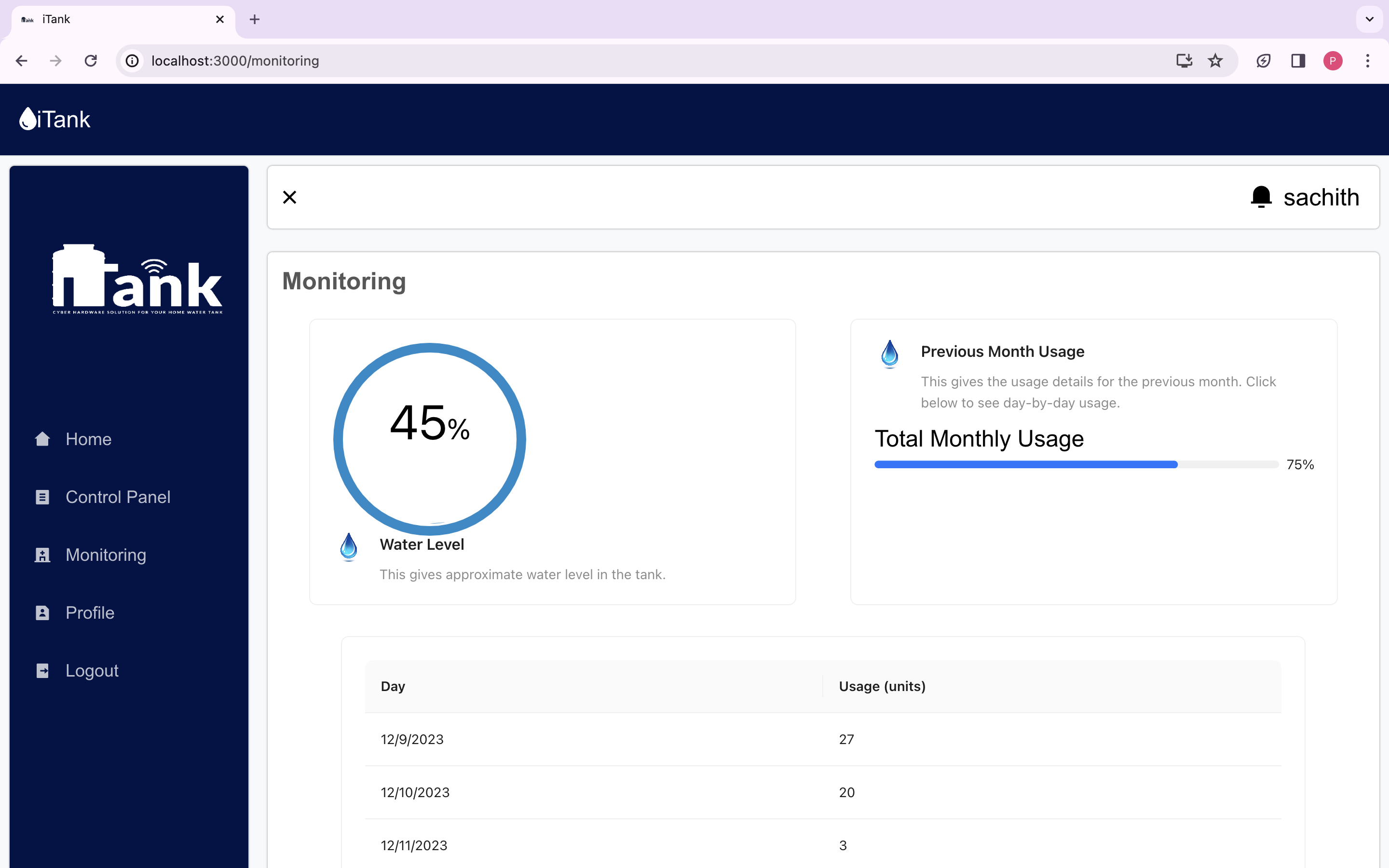
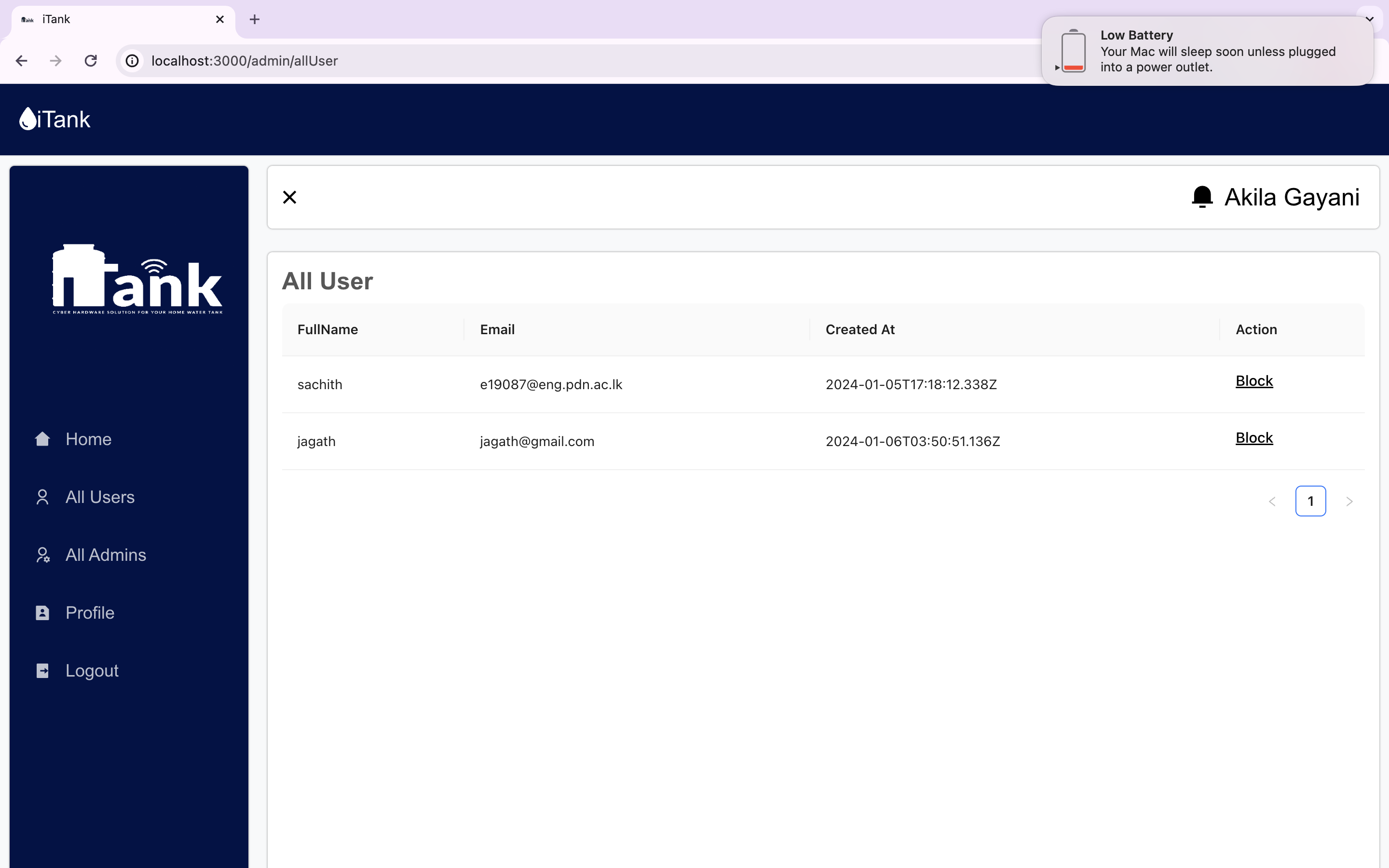
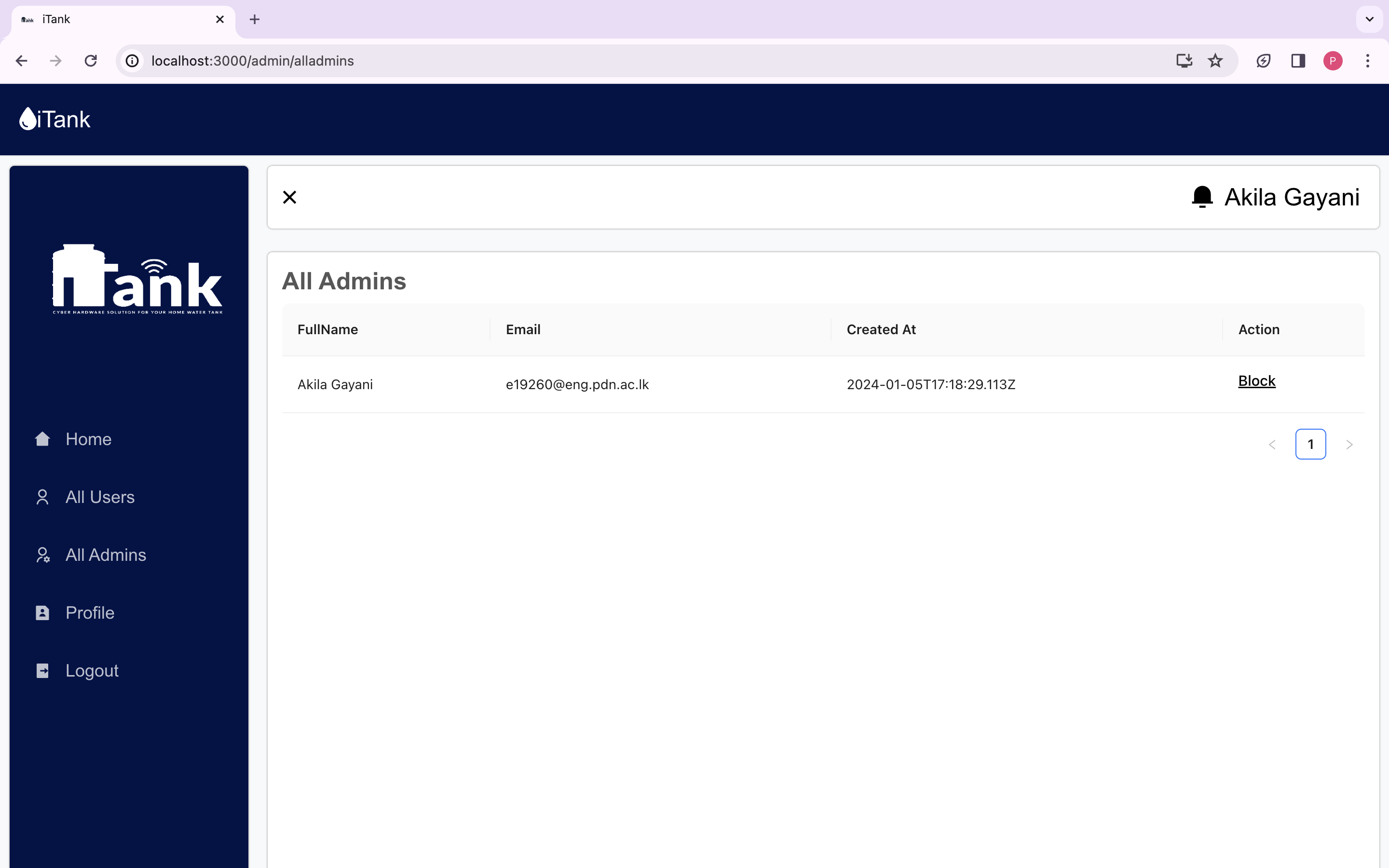
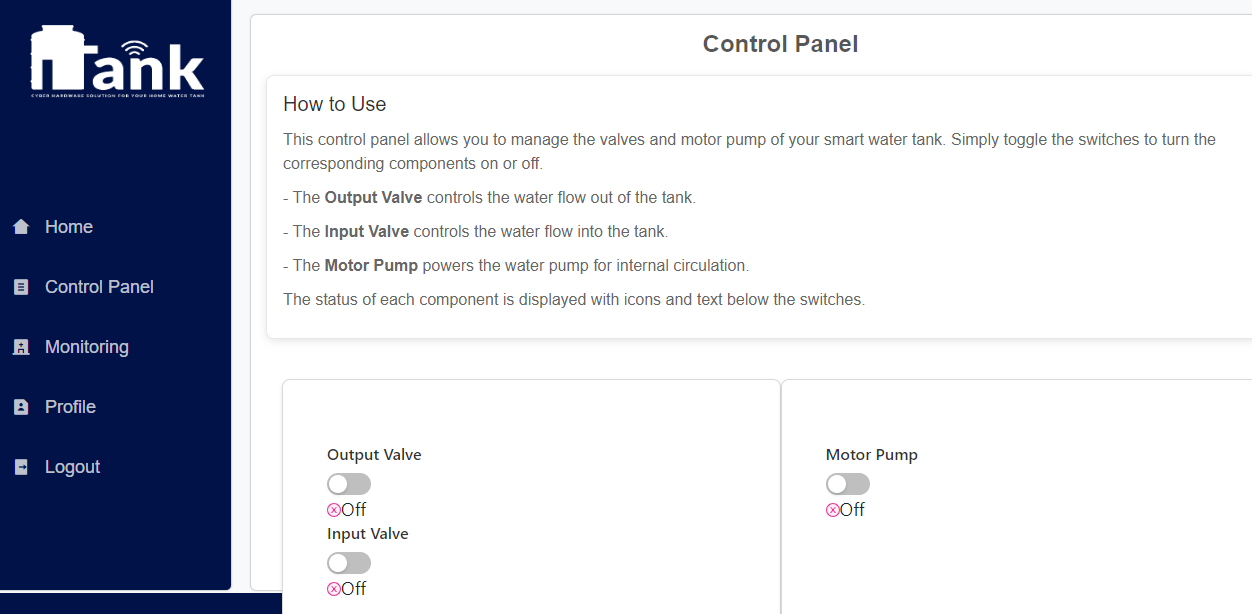
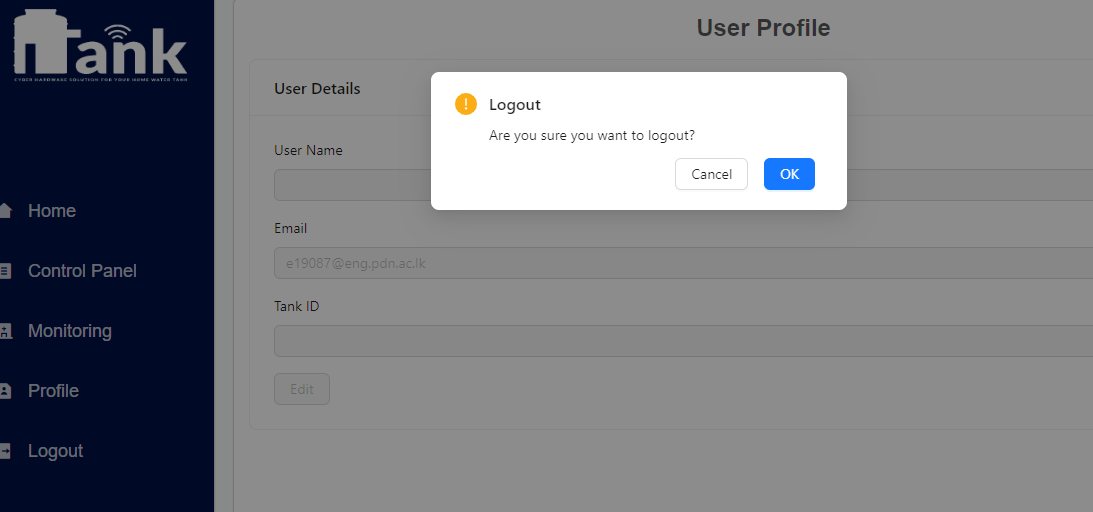
We are delighted to present the culmination of our dedicated efforts in the form of the final web application UI/UX images. These meticulously crafted visuals encapsulate the essence of our project, reflecting the seamless integration of design and functionality.

E/19/087

E/19/260

E/17/083

E/19/..

E/19/..