Introduction
For years, the need to protect one’s property has become one of people’s main concerns. The sense of security and protection is one of those feelings that makes us comfortable and complements quality living. Although there are existing solutions for home security like video surveillance cameras, alarms etc, they are very expensive, and the installation process is also not easy. Most of the existing security system solutions address the needs of the people who are living in private houses. But people who live in apartments in urban areas have some added needs to be satisfied with a particular security system. Therefore, addressing all these issues along with some added unique features we have come up with the idea of a Smart Apartment Security System. Smart Apartment security system is a system that secure entry points, like doors and windows, as well as interior spaces in an apartment from a burglary or a fire by notifying the owners and security officer at the apartment gate whenever a threat has been identified through a mobile application.
Learn More-
01
Mobile Application
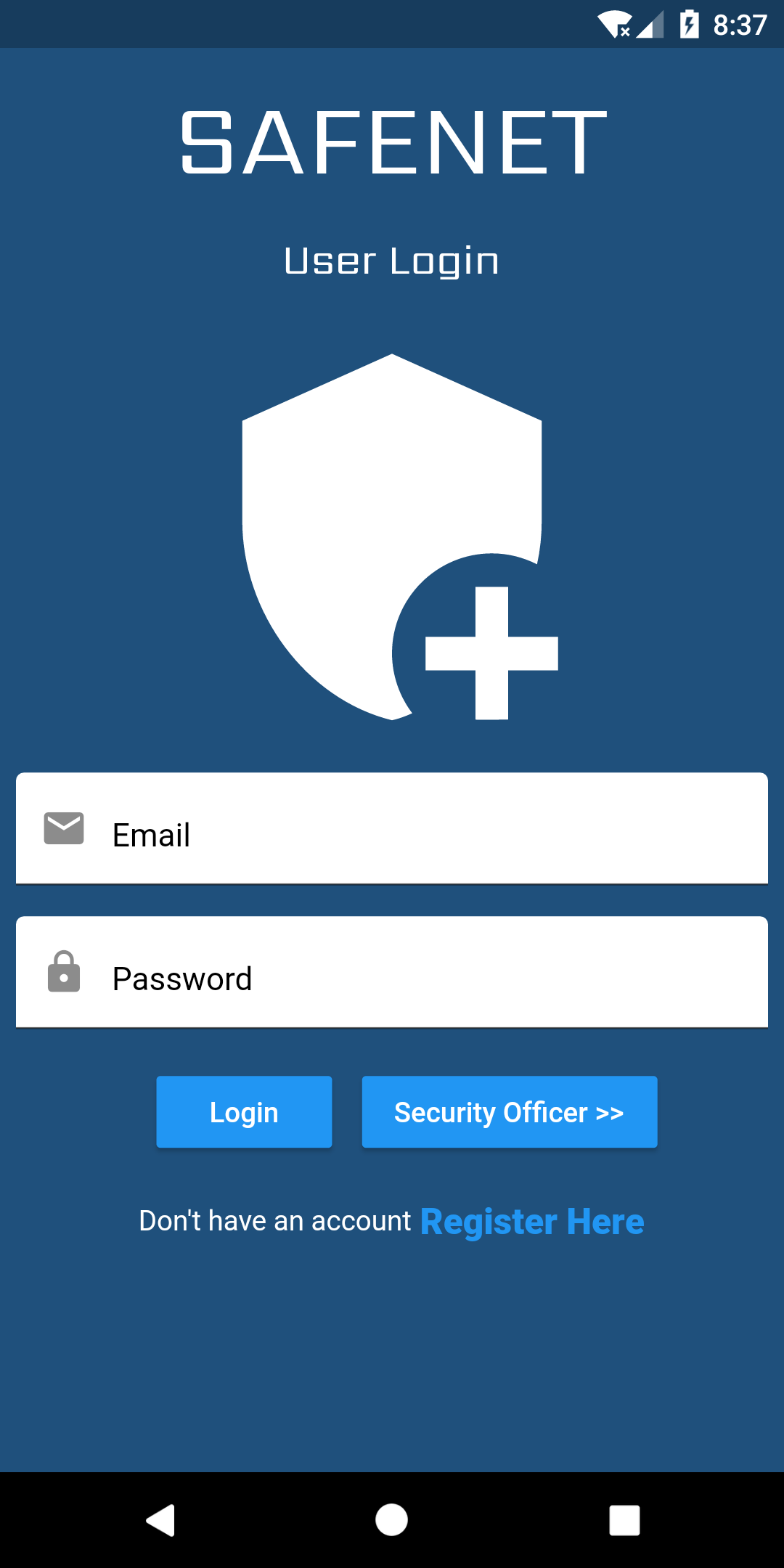
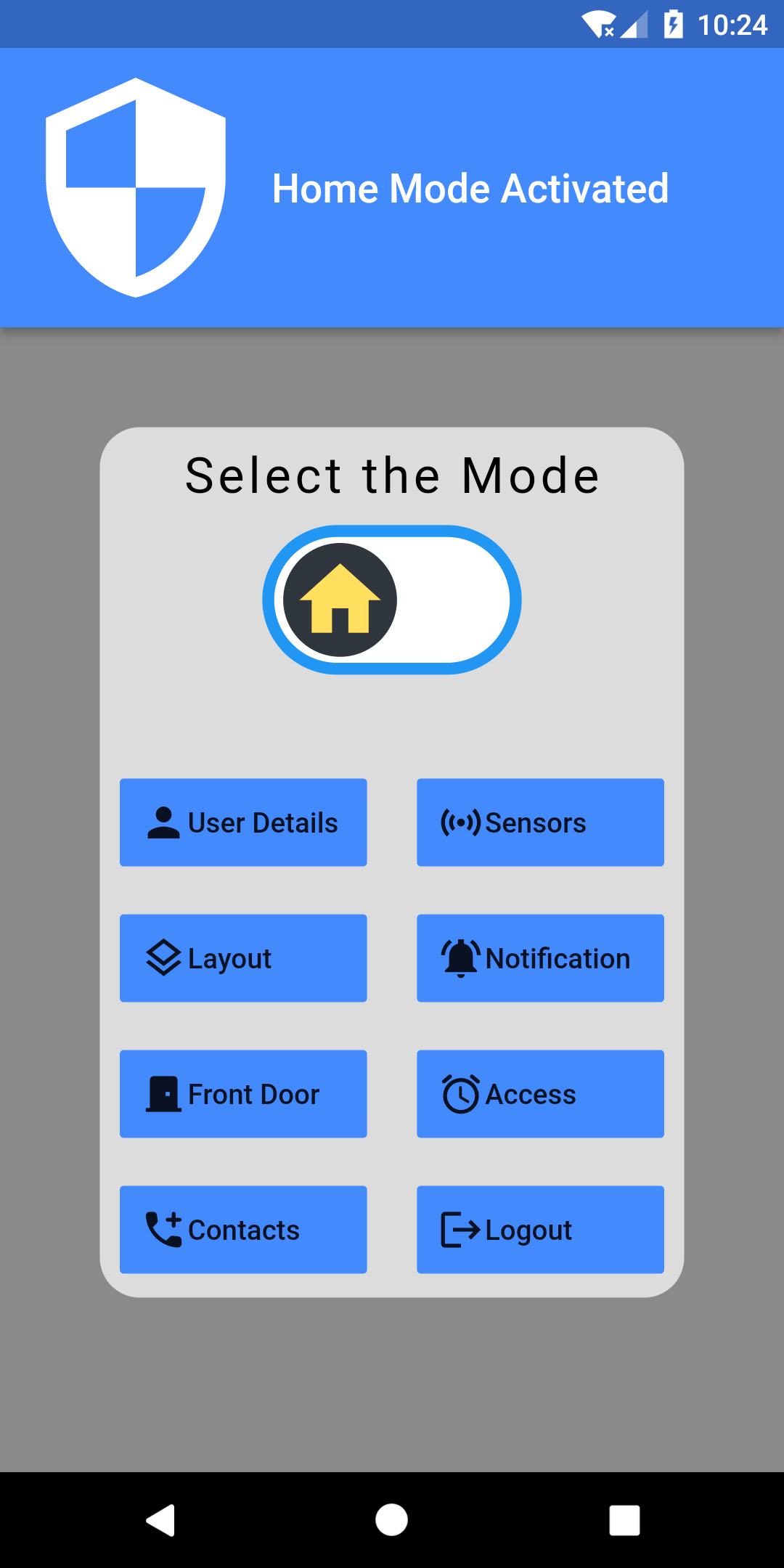
SafeHome security system to allow users to remotely monitor and control the security system. Users are able to arm and disarm the system, get mobile alerts and contact the security officer whenever a threat has been identified by the security system. Users can log in to the mobile app anytime to view the status of sensors, activity logs for door locks and more as well. The app is designed using Flutter.
-
02
Security System
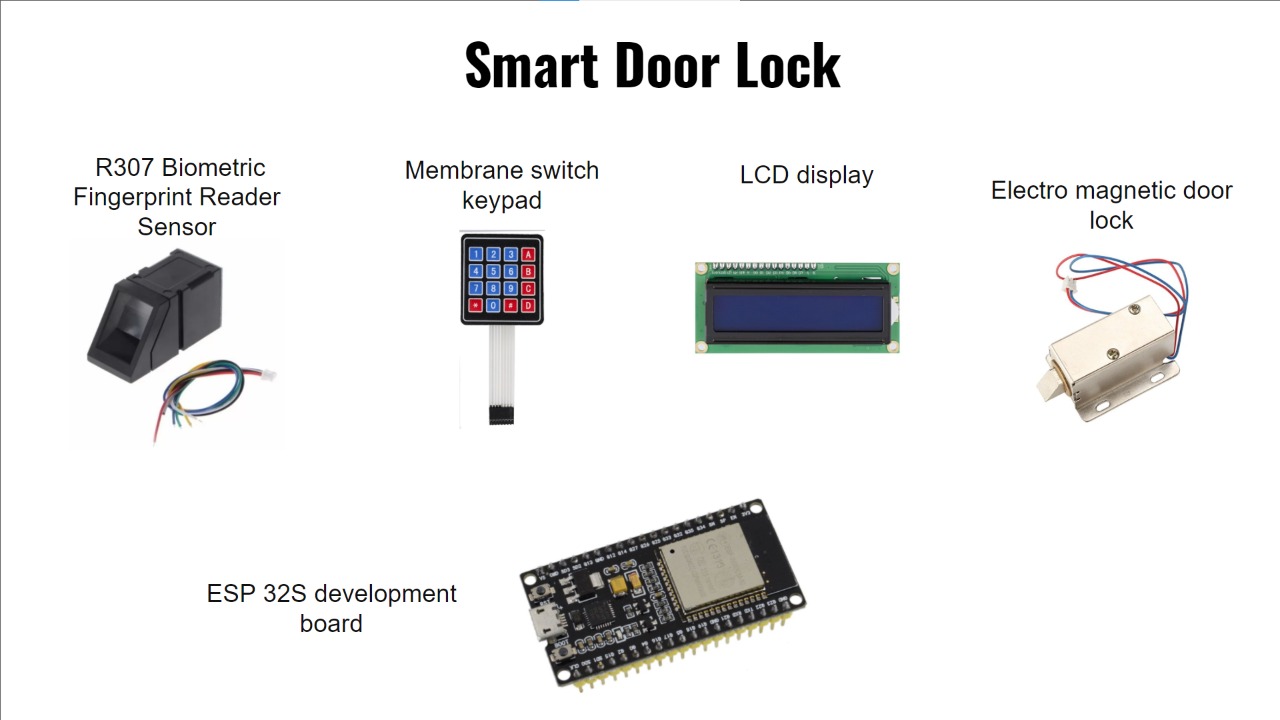
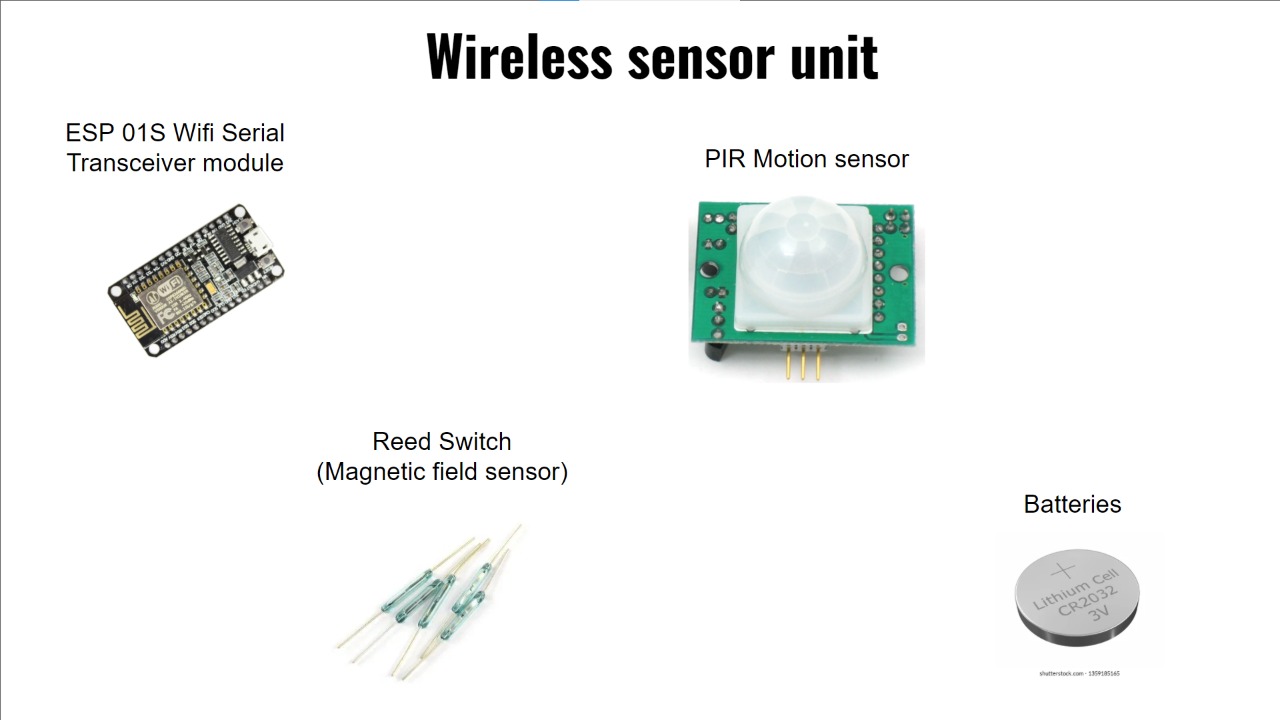
The security system is used to identify threats in the entry points and interior spaces of an apartment through sensors. It will consist of wireless sensors(door and window sensors, motion sensors, smoke detector), a siren and a smart door lock with fingerprint access for added security. ESP 32 development board is used as the microcontroller of the door lock and ESP-01S WiFi modules are used for wireless sensors.
-
03 Web
Server
AWS server is used as the web server for the SafeHome Security System. Signals from sensors are passed to the mobile application as well as control information from mobile applications are passed to the smart door lock and response mechanisms through this server. Database which is used to store sensor statuses and logs of the system is hosted at the server.
Infrastructure
Technologies
Frontend Development Flutter
As the front end development we use flutter as our front end development software in this development process the expectations are to provide user friendly and interesting interface with enhanced UI and UX experience to the client.Other than that cross platform support is required for us to maintain the target clients by giving them access to our services independant their mobile os type.
Backend Development NodeJs
In the backend server requires to handle a larger amount of requests. Therefore the scalability and sustainability if uncaught error exceptions happend are critical points under choosing a optimum backend server. For those requirements, Node js would be the best solution for this project. Therefore the backend server side requests managements are done by the NodeJs.
Cloud Deployment AWS
Due to financial issues met in the process of developing the physical server of maintaining cost. The team sole decision and the academic guidance as well based on cloud services. Therefore the cloud server deployment was decieded. In that case the EC2 instance of AWS server support is selected.
Database Development MySQL
For storing data puroposes' requirements were the structured schema with the same type of data that have the ability to contain all the details of the target market when the product able to cover the whole market itself. Also the data base should be able to scalable from a smaller database. For these requirements are fulfil when the chosen selection was Mysql. Because the mysql have the ability contain 1000 different tables and all our reqiurements are fulfilled under 1000 tables.
Circuit Diagrams
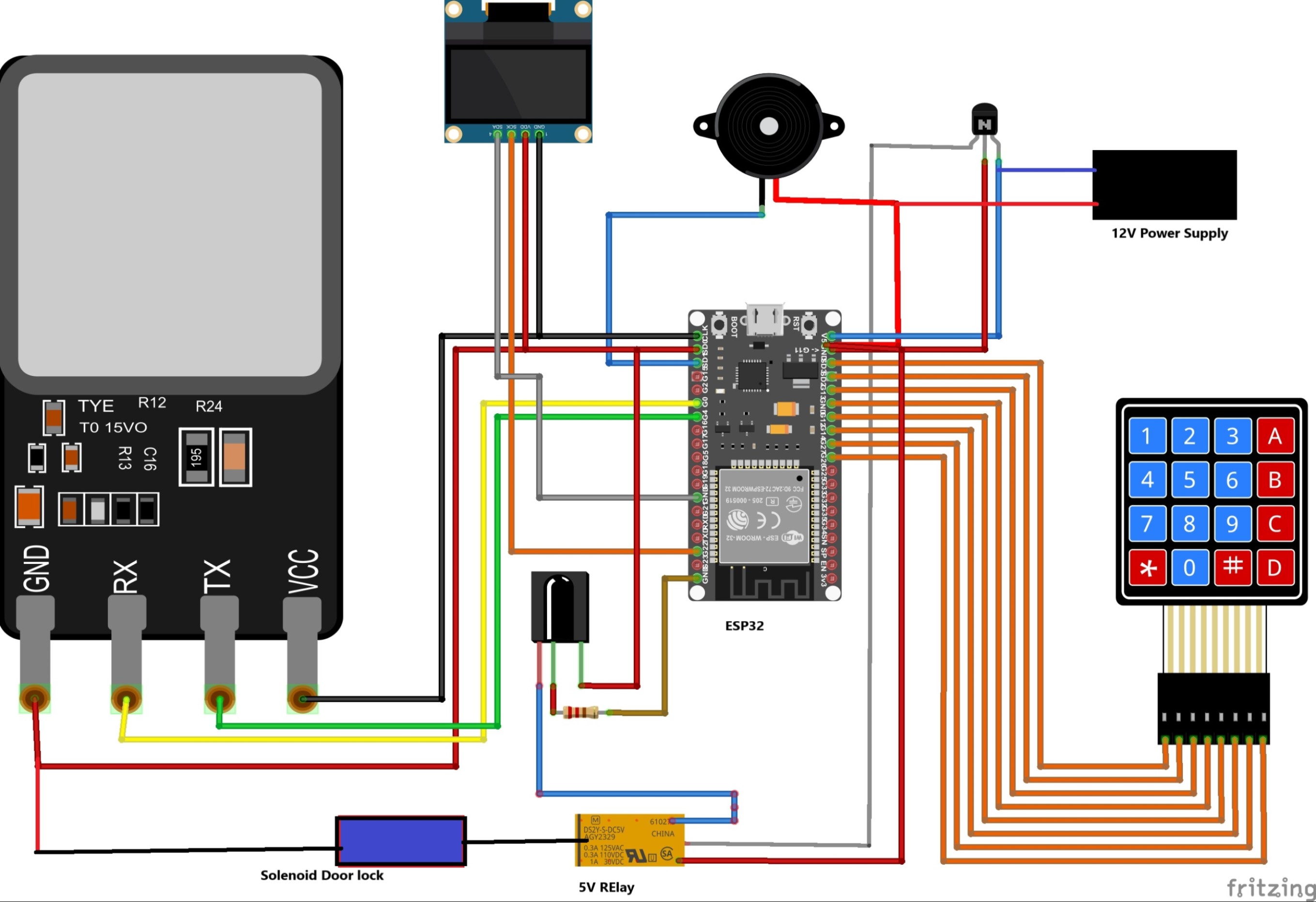
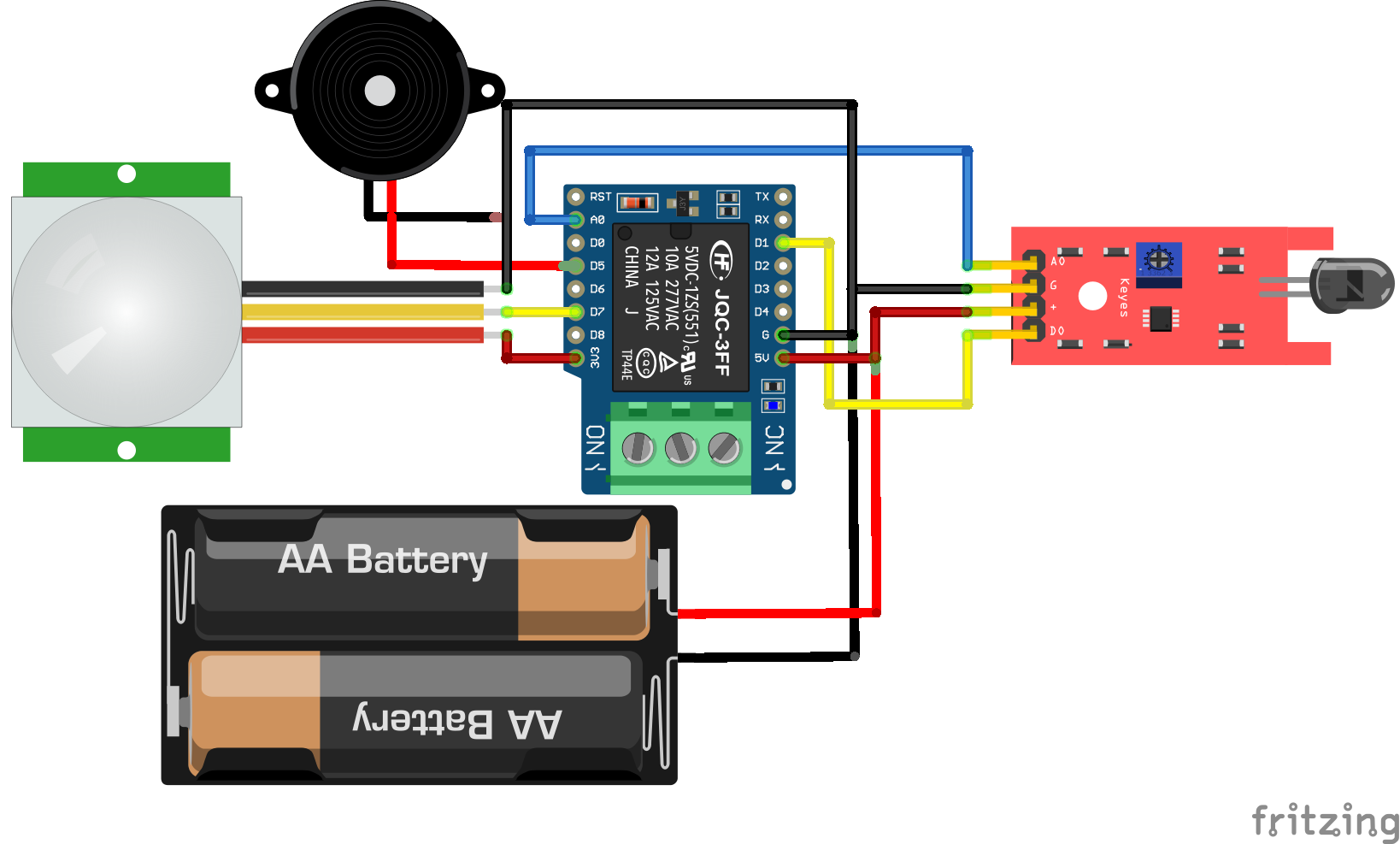
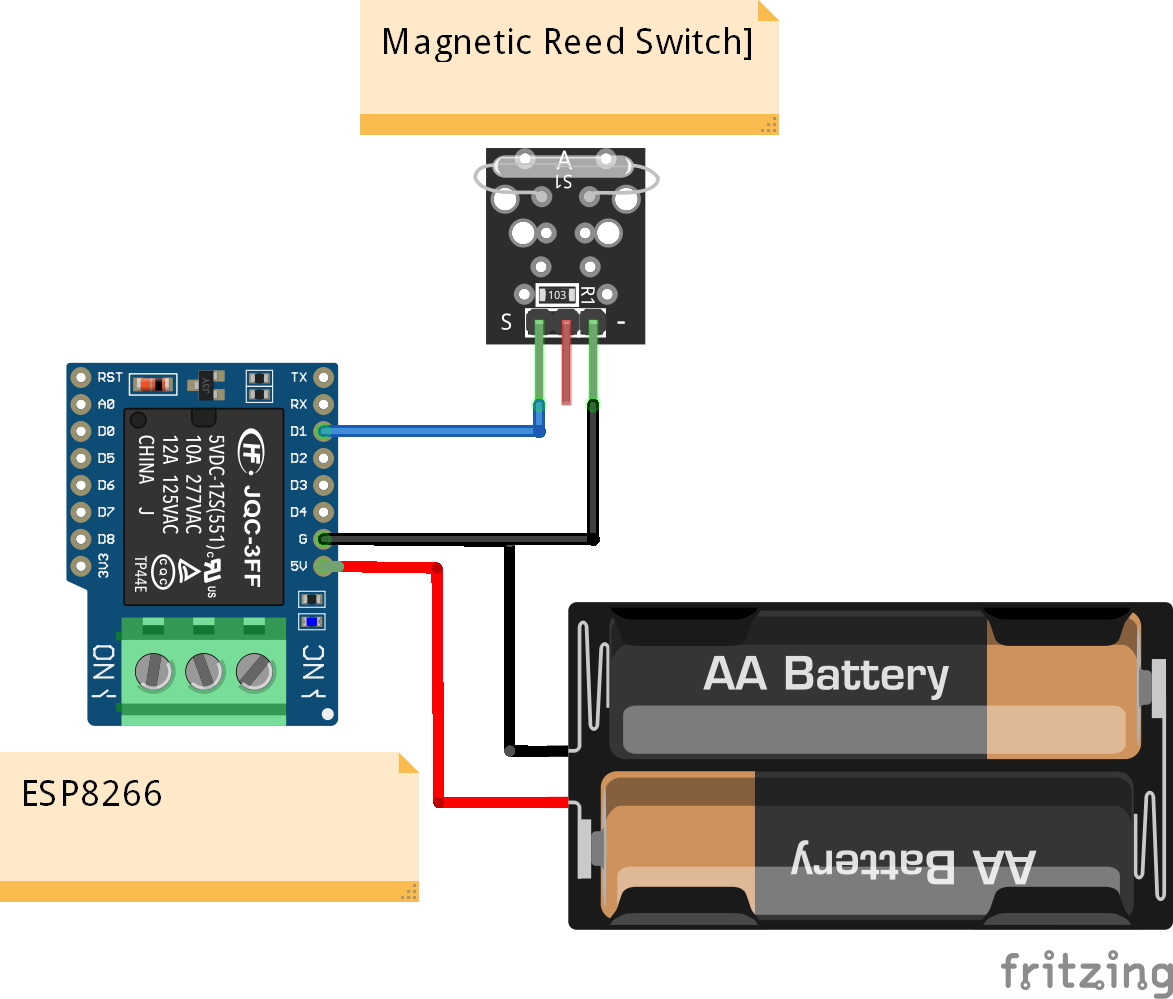
Schematic Diagrams
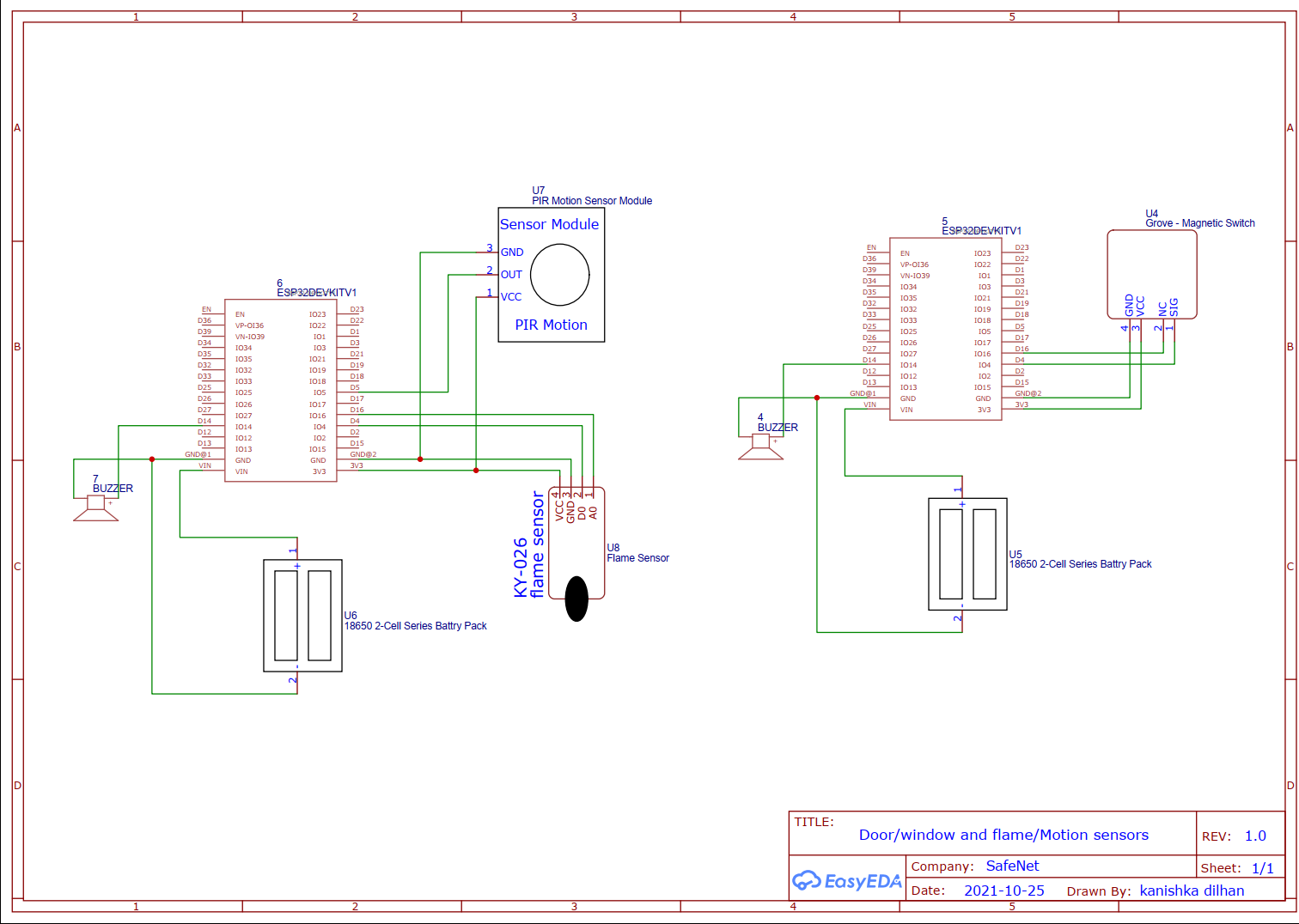
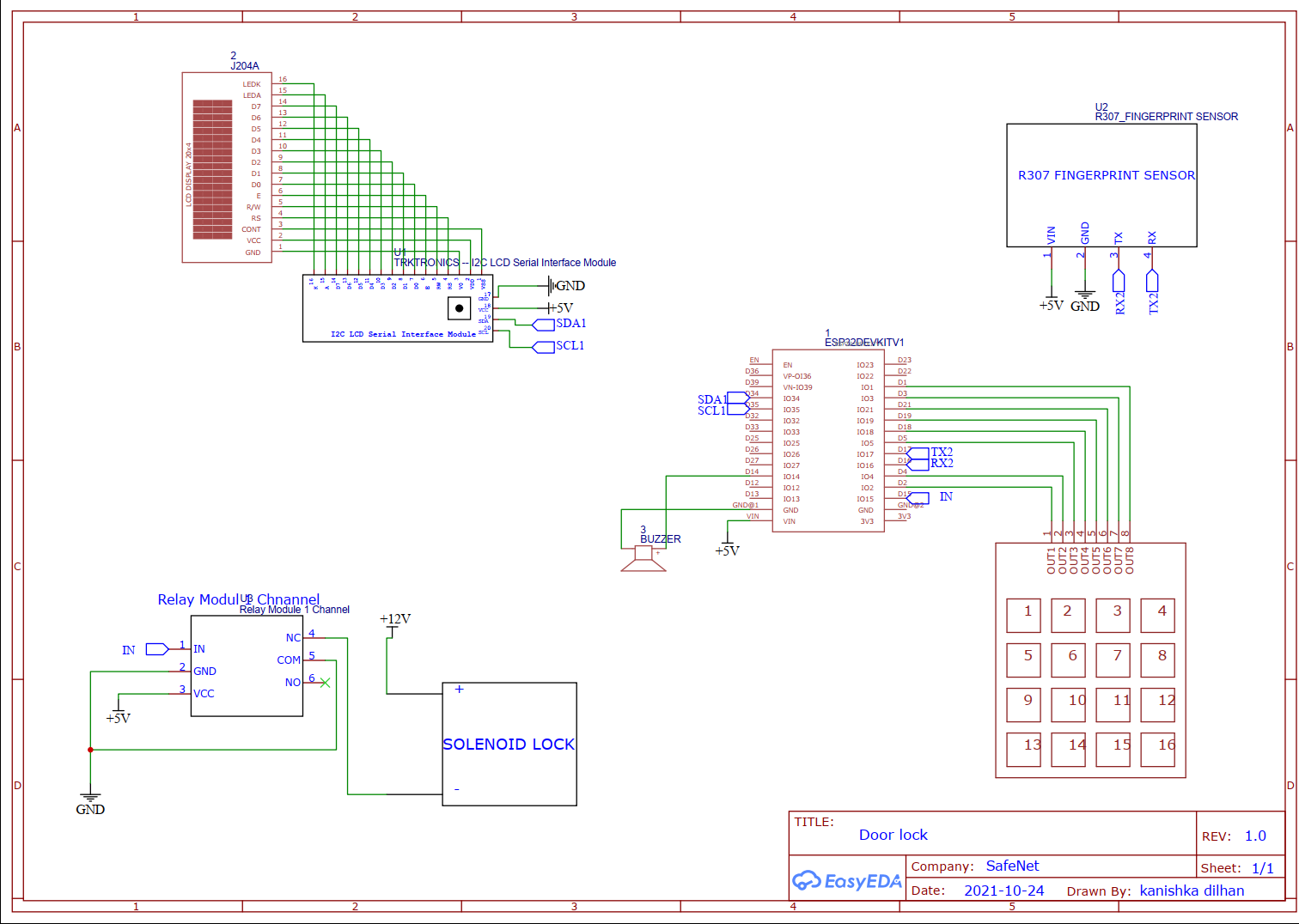
Hardware Designs
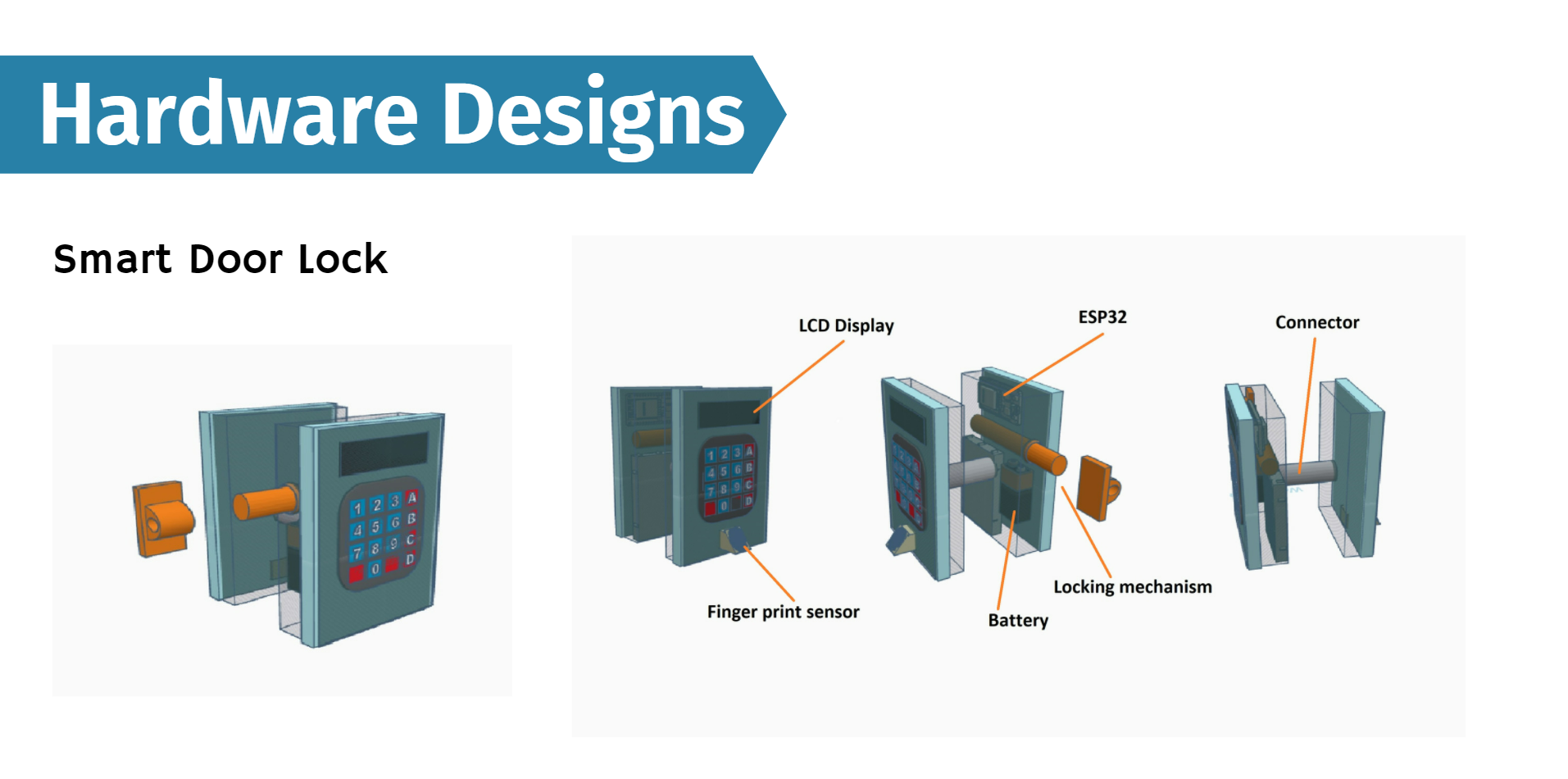
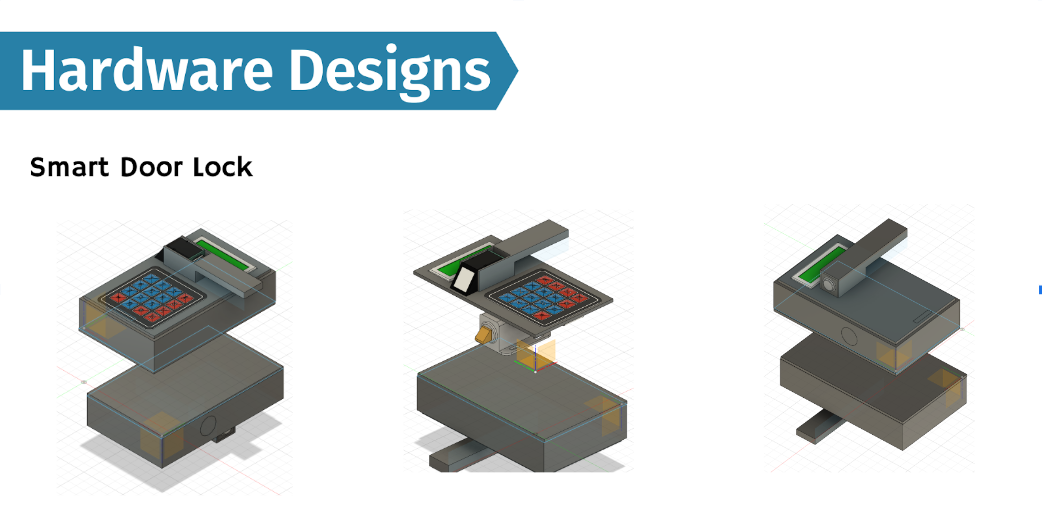
Hardware Design
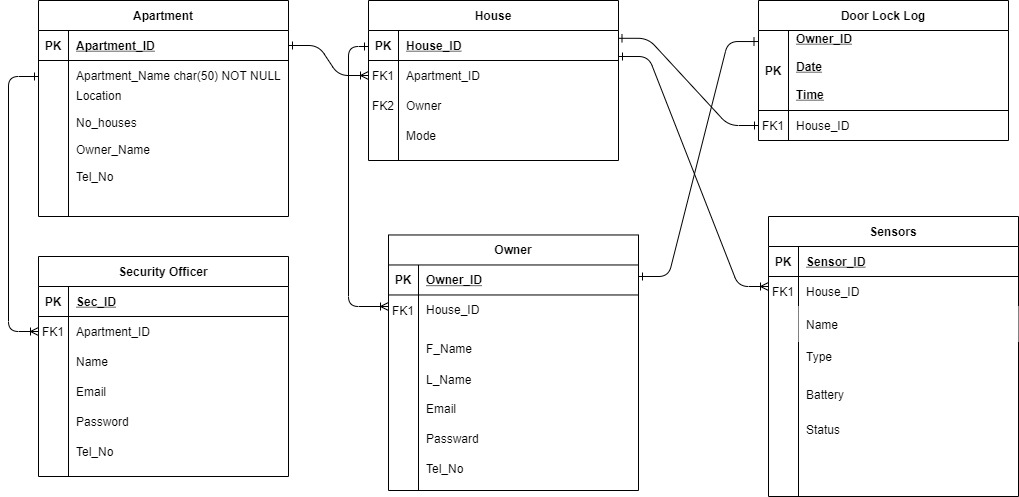
Watch VideoER Diagram and Relational Schema
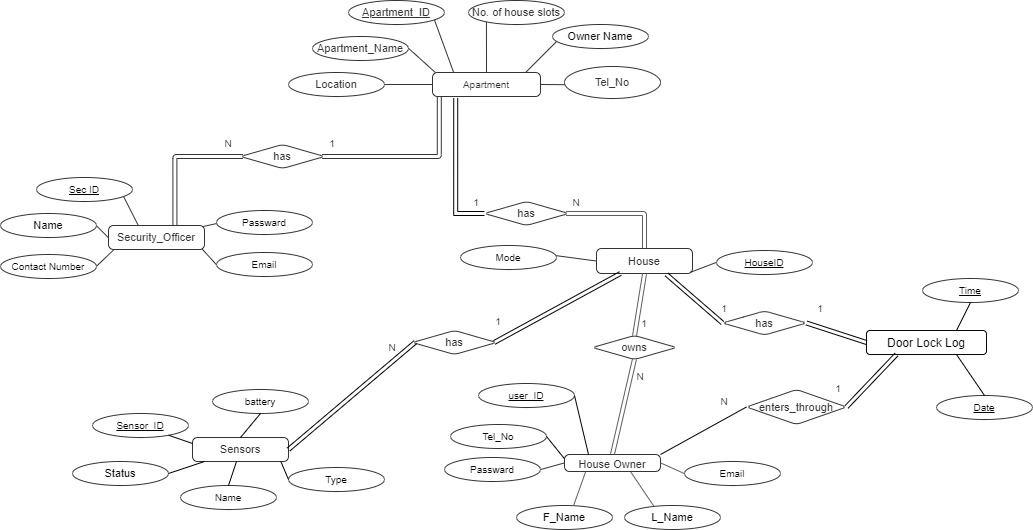
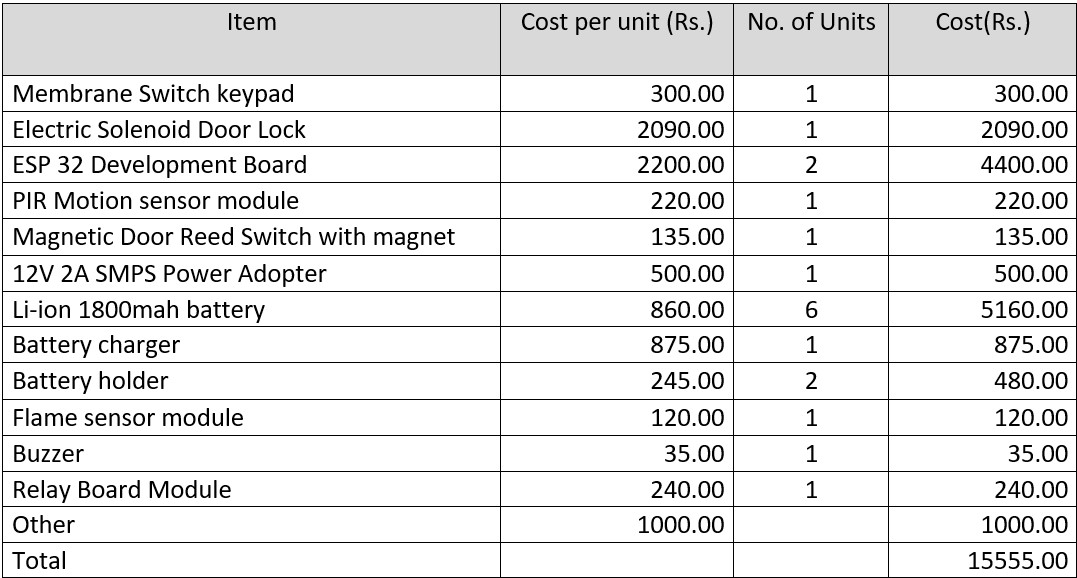
Detailed Budget
User Manual and Design Manual
UI/UX Designs
There is a mobile application for house owners and Security officers in the apartment and there is a web application for the administrator
- Mobile Application
- Web Application
Door Lock Installation
Watch VideoSensor Unit Installation
Watch VideoTesting Plan
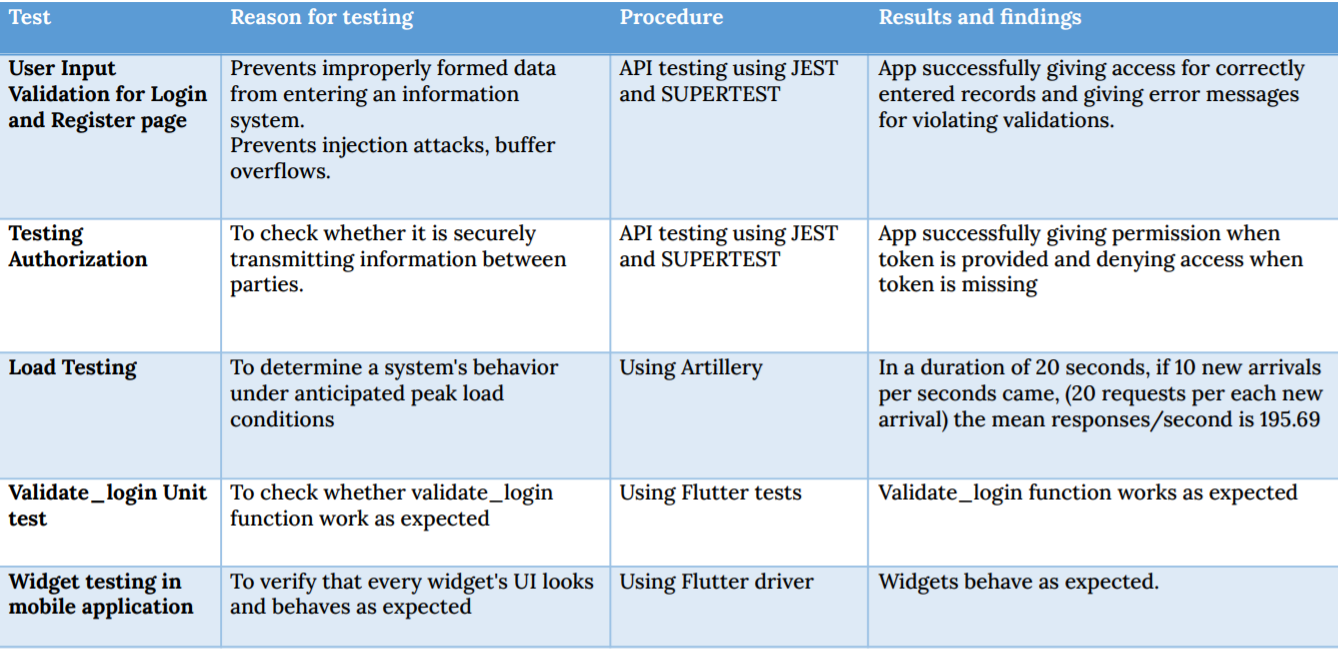
Testing
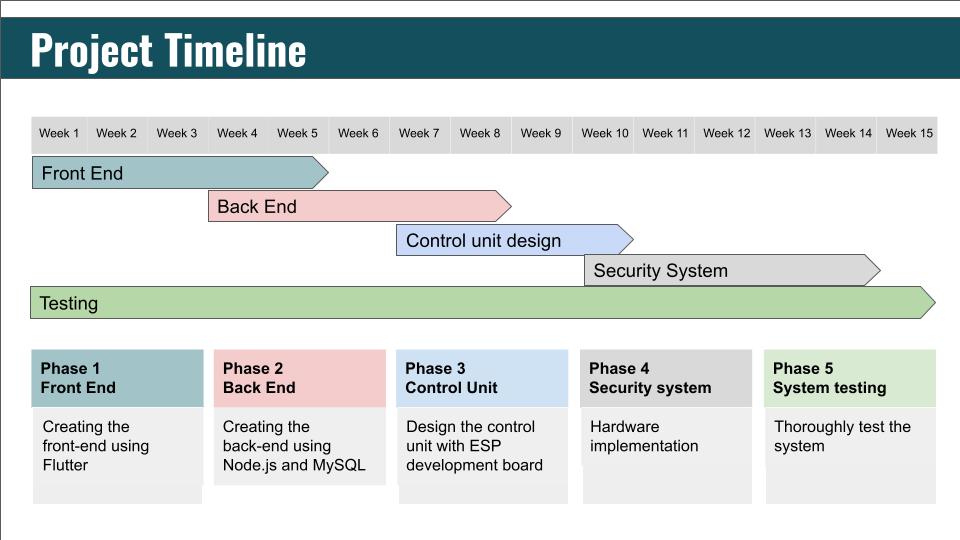
Watch VideoProject Timeline
Security
Security is the most important thing in the IT world right now. In our solution, we have deeply considered the security point of view of our system. We have developed our system with the help of the following techniques to enhance the application security in our solution.
-
JSON
Web Tokens (JWT)
Our application use JSON Web Tokens (JWT) to allow the client to indicate its identity for further exchange after authentication. It is a self-contained way for securely transmitting information between parties.
-
User Input validation
This prevents improperly formed data from entering an information system. Because it is difficult to detect a malicious user who is trying to attack software, applications should check and validate all input entered into a system specially in Resgistration and Login. Input validation as a mitigation strategy for both SQL injection and XSS.
-
Two
Factor Authentication
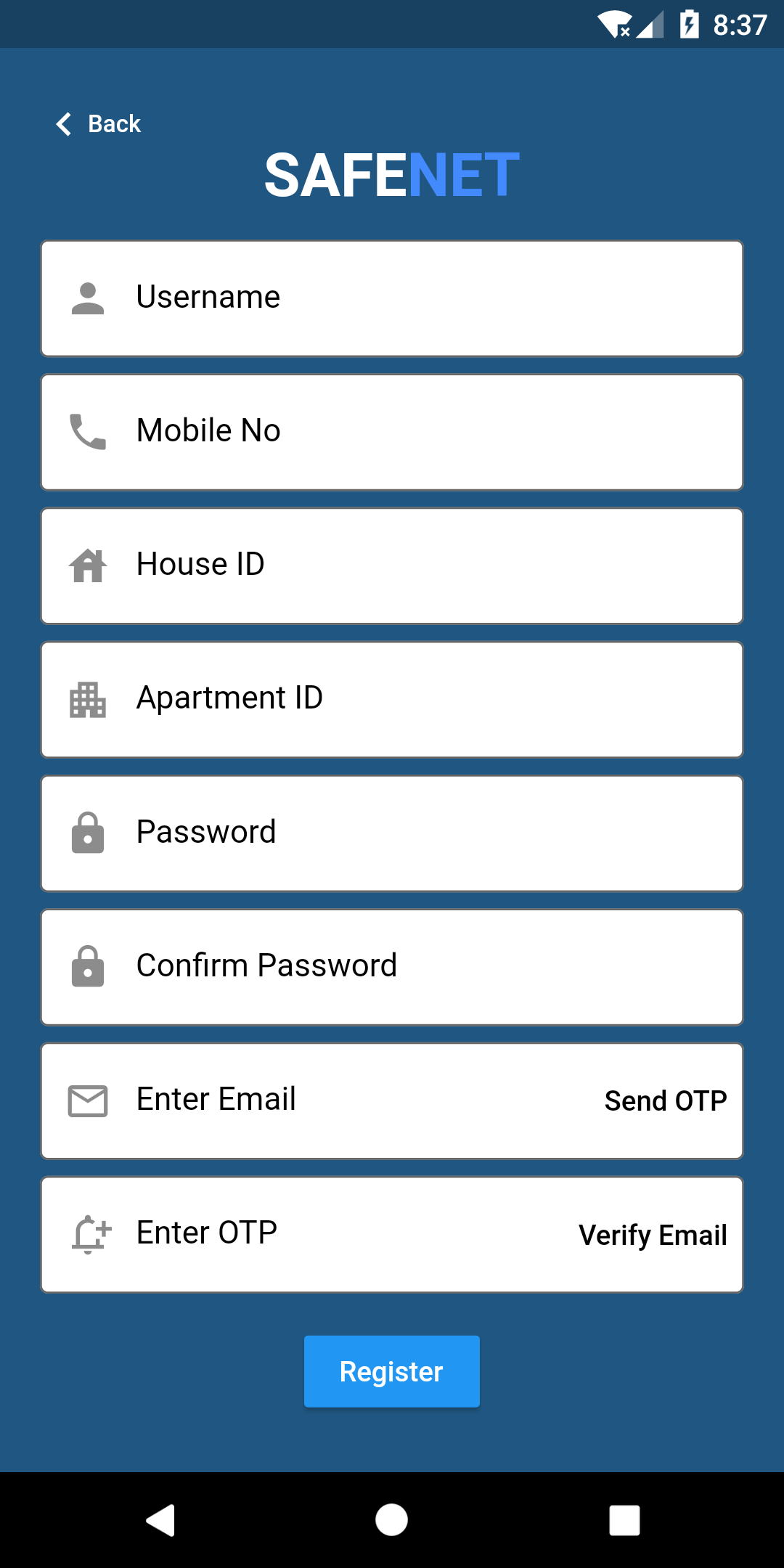
Used in Authentication is used in the Registration of the Mobile Application. When Email is provided, OTP is sent to email address and user has to Enter that OTP for the registration.
-
Password Hashing
Password hashing is used in our application to verify the integrity of passwords, sent during login, against the stored hash so that actual passwords never has to be stored. A salt is added to the hashing process to force their uniqueness, increase their complexity without increasing user requirements, and to mitigate password attacks like hash tables.
-
AWS
EC2 Security Groups
A custom security group is assigned to the instance where our application is deployed which allows only http/tcp connections on port 80. Security groups offer protection at the ports and protocol access level.
Mobile Application Demo
Watch VideoWeb Application Demo
Watch VideoOur Team Members

Dananjaya Morais
Undergraduate - Department of Computer EngineeringUniversity of Peradeniya

Ishini Udara
Undergraduate - Department of Computer EngineeringUniversity of Peradeniya

Kanishka Dilhan
Undergraduate - Department of Computer EngineeringUniversity of Peradeniya
Our Advicors

Dr.Isuru Nawinne
Senior Lecturer - Department of Computer EngineeringUniversity of Peradeniya

Dr. Mahanama Wickramasinghe
Senior Lecturer - Department of Computer EngineeringUniversity of Peradeniya